Lucky MVP 13
Troy Hunt
JULY 13, 2023
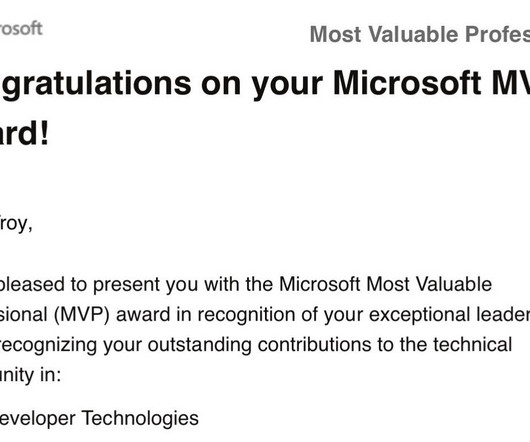
Each year since 2011, Microsoft has sent me a lovely email around this time: I've been fortunate enough to find a passion in life that has allowed me to do what I love and make a great living out of it all whilst contributing to the community in a meaningful and impactful way. In last year's MVP announcement blog post , I talked about one of my favourite contributions of all that year being the Pwned Passwords ingestion pipeline for the FBI.






































Let's personalize your content