Zero-Click iPhone Exploits
Schneier on Security
SEPTEMBER 1, 2021
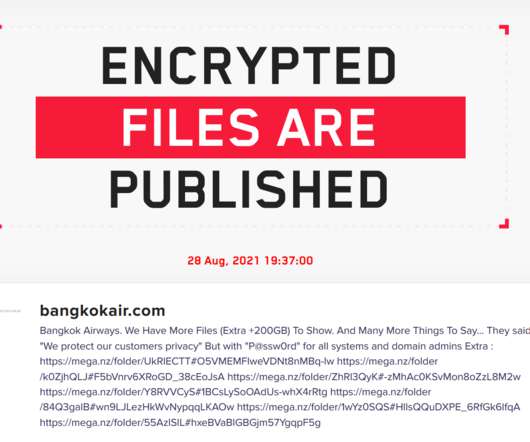
Citizen Lab is reporting on two zero-click iMessage exploits, in spyware sold by the cyberweapons arms manufacturer NSO Group to the Bahraini government. These are particularly scary exploits, since they don’t require to victim to do anything, like click on a link or open a file. The victim receives a text message, and then they are hacked. More on this here.








































Let's personalize your content