SolarWinds Security Event Manager – SIEM Product Overview and Insight
eSecurity Planet
FEBRUARY 6, 2023
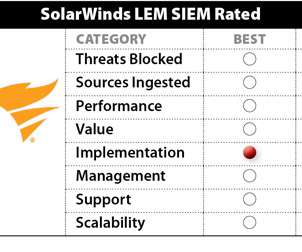
SolarWinds Security Event Manager (SEM) 2022.4 SolarWinds SIEM Features Rated Threats Blocked: Good. SolarWinds SEM also integrates with online threat feeds and can notify and respond to inbound/outbound traffic and authentication attempts with known bad IP addresses for threats such as ransomware, malware, spam, phishing, and more.

















































Let's personalize your content