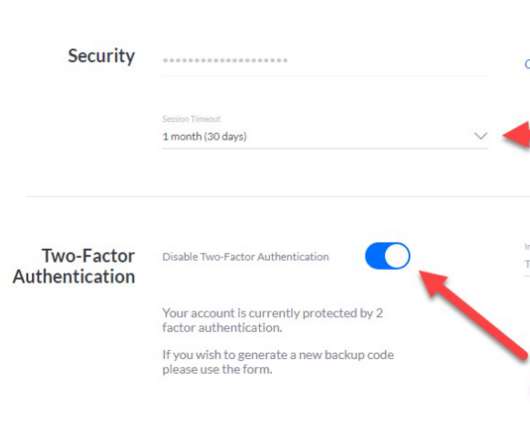
Samsung offers Mobile Security protection as below
CyberSecurity Insiders
NOVEMBER 25, 2021
From backdoors- As the Korean giant creates, validates and manufactures its computing devices all on its own, its every piece of hardware, wiring and firmware is securely drafted at its high secure R&D plants & factories in the world. So, the question of unauthorized backdoors being present on any of its devices gets eliminated.














































Let's personalize your content