Malware exploits undocumented Google OAuth endpoint to regenerate Google cookies
Security Affairs
JANUARY 1, 2024
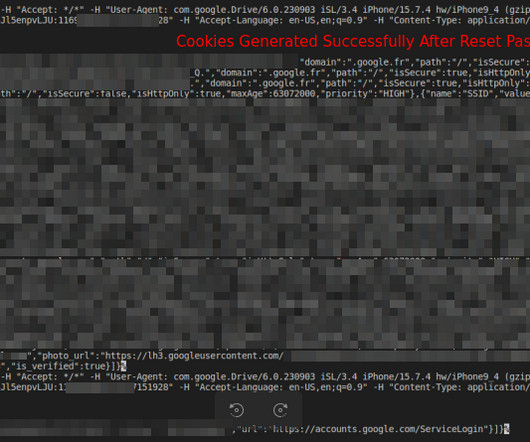
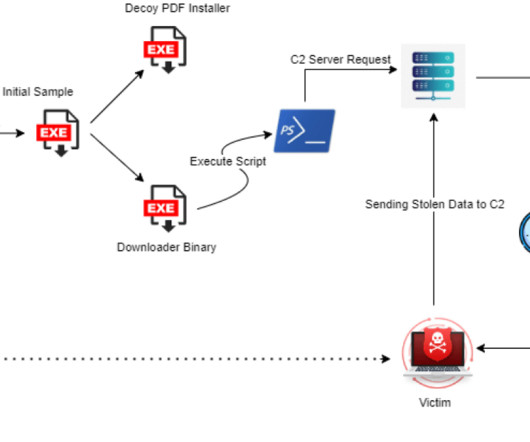
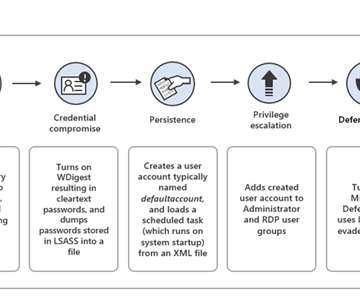
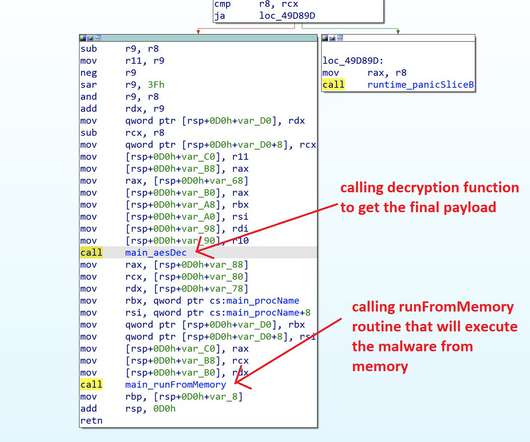
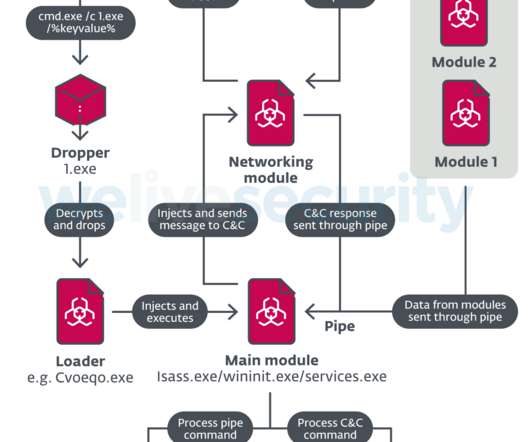
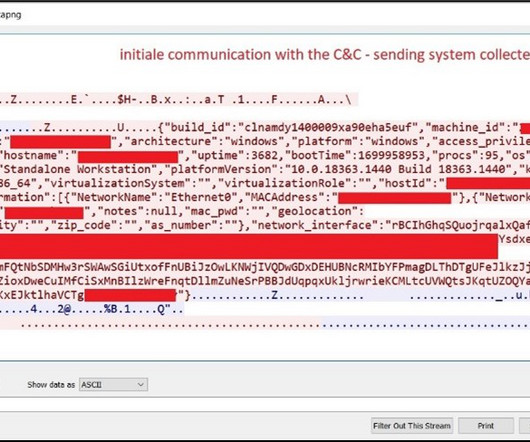
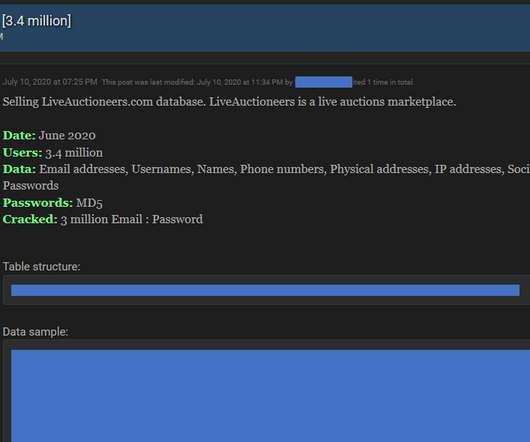
An attacker can use the exploit to access Google services, even after a user’s password reset. Subsequently, other malware integrated the exploit, including Rhadamanthys, Risepro, Meduza , Stealc Stealer and recently the White Snake. The experts pointed out that the exploit works even after users have reset their passwords.































Let's personalize your content