The Best 10 Vendor Risk Management Tools
Centraleyes
MARCH 25, 2024
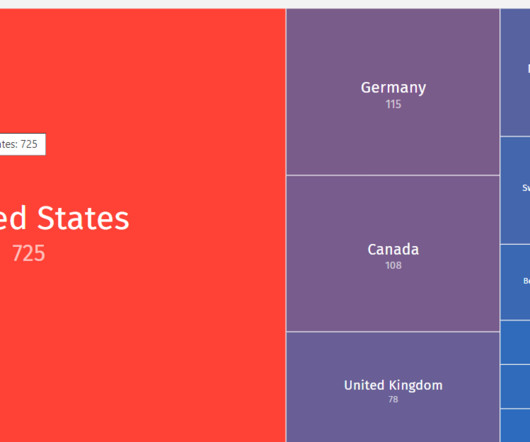
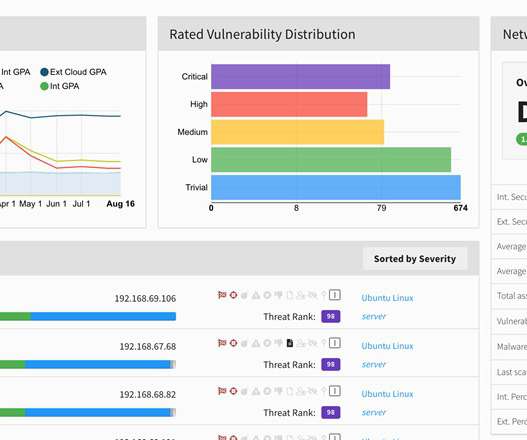
Let’s discuss an acronym reshaping the business world: Vendor Risk Management , or VRM. Once an abbreviation that few knew the meaning of, VRM is now a basic component of responsible business processes. Times have changed, and VRM applies to everyone, not just the big players. What compliance standards do you need to meet?
















































Let's personalize your content