Another 0-Day Looms for Many Western Digital Users
Krebs on Security
JULY 2, 2021
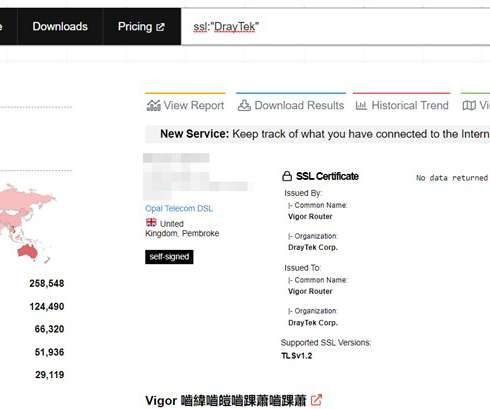
But there is a similarly serious zero-day flaw present in a much broader range of newer Western Digital MyCloud network storage devices that will remain unfixed for many customers who can’t or won’t upgrade to the latest operating system. “We strongly encourage moving to the My Cloud OS5 firmware,” the statement reads.

















































Let's personalize your content