Kazakhstan Government Intercepting All Secured Internet Traffic
Adam Levin
JULY 19, 2019
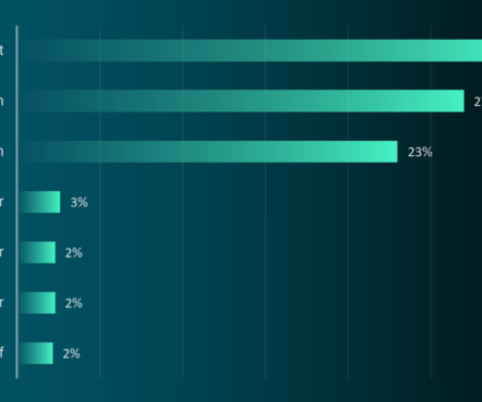
The Kazakhstan government is intercepting all HTTPS-encrypted internet traffic within its borders. Under a new directive effective 7/17, the Kazakhstan government is requiring every internet service provider in the country to install a security certificate onto every internet-enabled device and browser.













































Let's personalize your content