Managing technology risk
CyberSecurity Insiders
JUNE 6, 2023
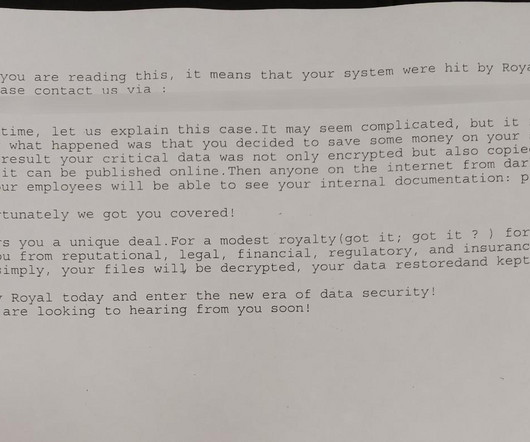
Numerous risks are inherent in the technologies that all organizations use. These risks have especially become apparent with recent ransomware attacks, which have crippled major infrastructure such as the Colonial Pipeline in the Eastern United States 1. The first part of GRC is governance.
















































Let's personalize your content