Chinese Android phones shipped with malware-laced WhatsApp, Telegram apps
Security Affairs
APRIL 16, 2025
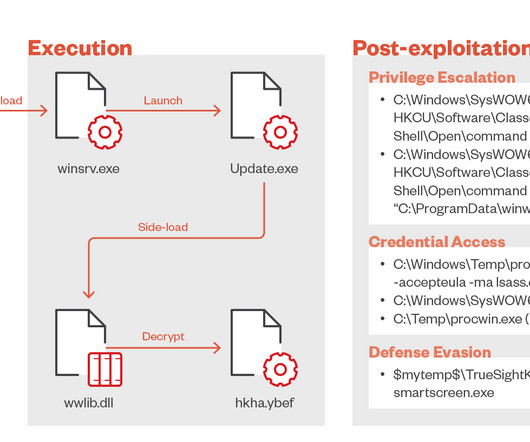
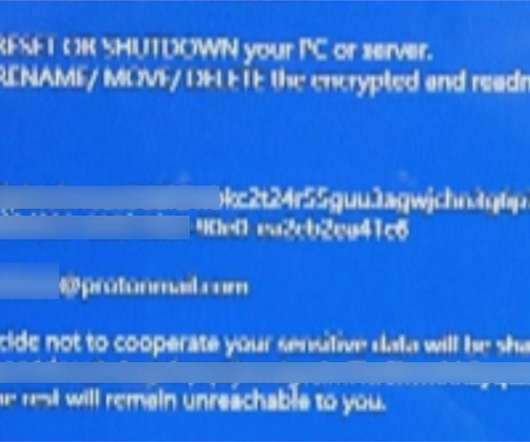
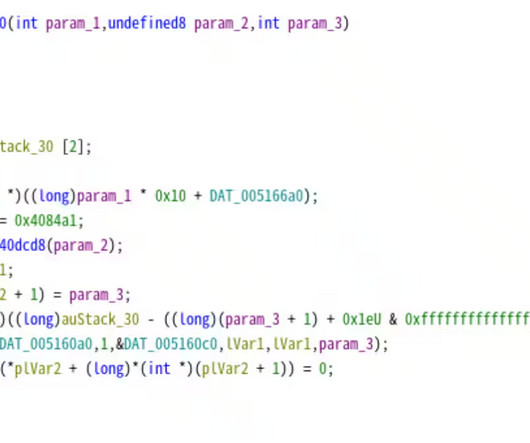
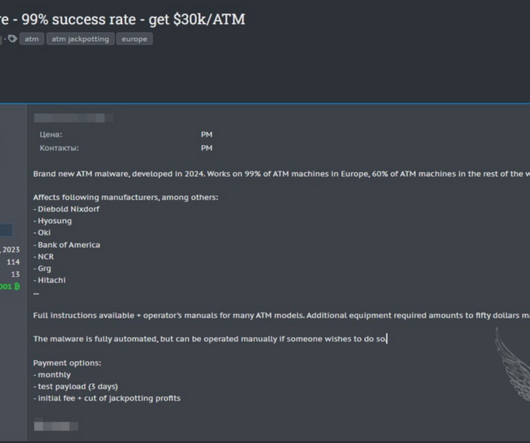
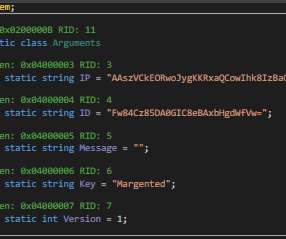
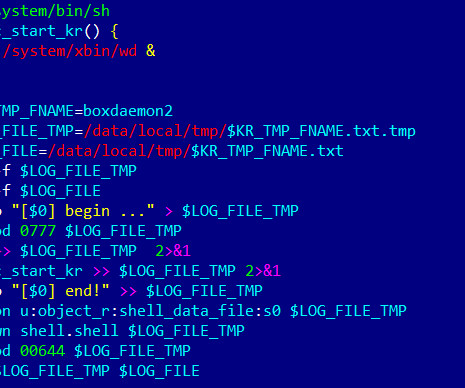
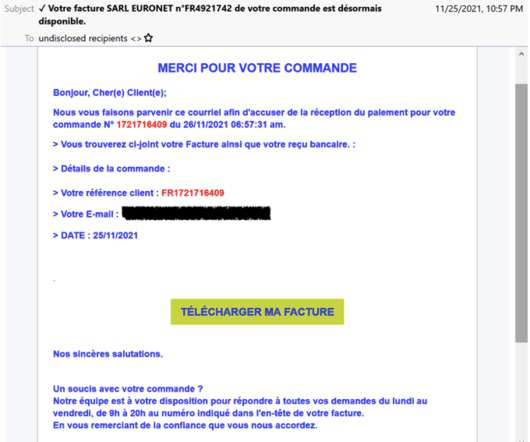
Attackers infiltrated the supply chain, embedding malware in pre-installed apps. Doctor Web warns that the attackers gained access to the supply chain of a number of Chinese manufacturers of Android-based smartphones. The experts found malware-laced applications pre-installed on the phone. ” continues the report.


























Let's personalize your content