The Pipeline Attack – Is Log Analysis Enough for Cybersecurity?
CyberSecurity Insiders
JULY 19, 2021
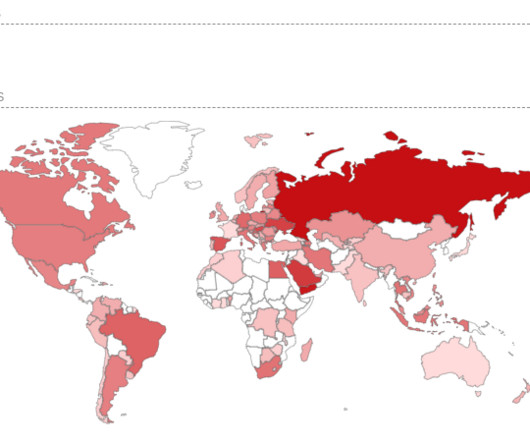
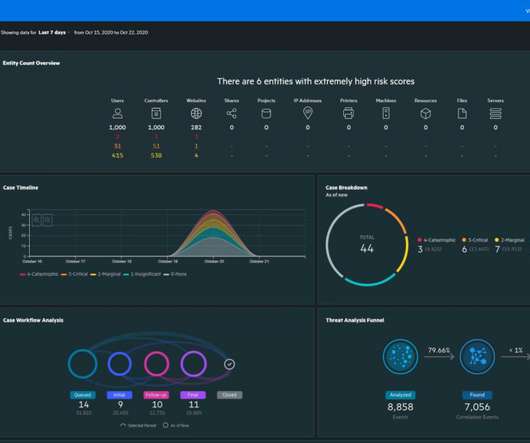
Many MSSP’s use SIEMs and other log management/aggregation/analysis solutions for cybersecurity visibility, but is log analysis enough? Let’s take a quick look at what we get from logs, and what we don’t get from logs. Logs by their very nature are a view into the past.











































Let's personalize your content