CyberGhost vs ExpressVPN (2024): Which VPN Is Better?
Tech Republic Security
AUGUST 19, 2024
While CyberGhost VPN presents an impressive amount of servers, ExpressVPN’s consistent VPN speeds and strong third-party audits give it the edge.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
AUGUST 19, 2024
While CyberGhost VPN presents an impressive amount of servers, ExpressVPN’s consistent VPN speeds and strong third-party audits give it the edge.
Security Affairs
JANUARY 24, 2025
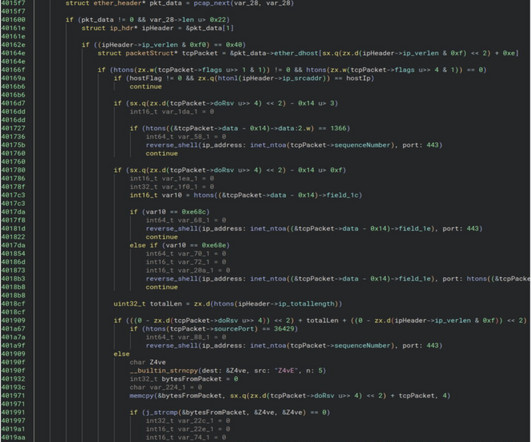
Lumen’s telemetry shows that roughly 50% of the targeted enterprise devices are configured as a virtual private network (VPN) gateway. The J-magic campaign is notable for targeting JunoOS, a FreeBSD-based operating system that threat actors rarely target in malware attacks. ” concludes the report.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Duo's Security Blog
APRIL 17, 2025
As many a podcast host will tell you, its about time you used a consumer or personal Virtual Private Network (VPN). VPNs have become commonplace, serving various purposes from the noble, like protecting an individuals digital footprint, to the dubious, like accessing geo-restricted content.

Krebs on Security
FEBRUARY 19, 2020
It is perhaps best known for selling virtual private networking (VPN) software that lets users remotely access networks and computers over an encrypted connection. Resecurity also presented evidence that it notified Citrix of the breach as early as Dec. 28, 2018, a claim Citrix initially denied but later acknowledged.
Security Affairs
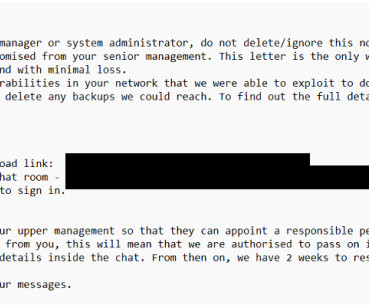
NOVEMBER 9, 2024
Attackers accessed targets via VPN gateways lacking multifactor authentication, some of which ran outdated software. In each of the cases, attackers initially accessed targets using compromised VPN gateways without multifactor authentication enabled. Some of these VPNs were running unsupported software versions.”
Security Affairs
NOVEMBER 27, 2020
The global impact of the Fortinet 50.000 VPN leak posted online, with many countries impacted, including Portugal. A compilation of one-line exploit tracked as CVE-2018-13379 and that could be used to steal VPN credentials from nearly 50.000 Fortinet VPN devices has posted online. Geomap of impacted countries.

Security Affairs
SEPTEMBER 25, 2020
According to SAM Seamless Network , over 200,000 businesses are using Fortigate VPN with default settings, exposing them to the risk of a hack. In response to the spreading of Coronavirus across the world, many organizations deployed VPN solutions, including Fortigate VPN, to allow their employers to work from their homes.
Troy Hunt
MARCH 5, 2021
Not just data breaches, but noteworthy data breaches; the VPN ones for being pretty shady, Oxfam because it included my data which was posted to a hacking forum, Ticketcounter because of the interactions I had with them during the disclosure process and Gab because, well, everything about Gab is always weird.

CyberSecurity Insiders
FEBRUARY 16, 2021
Published in collaboration with the Cybersecurity Insiders, the report includes findings from a global survey of more than 350 cybersecurity professionals on the current state of remote access environments, the rise in VPN vulnerabilities, and the role zero-trust security models play in providing access to enterprise applications.

eSecurity Planet
NOVEMBER 4, 2021
The many solutions available mirror the breadth of possible use cases, but we can achieve a high-level understanding by reviewing the four most common solutions: RDP, VPN, VDI, and DaaS. All these technologies can present security challenges, which makes zero trust principles important in any remote access solution. It Depends.

SecureBlitz
NOVEMBER 13, 2023
In this post, I will reveal the Private Internet Access VPN Black Friday deal. Welcome, cyber guardians of SecureBlitz, to a cybersecurity revolution brought to you by Private Internet Access VPN's Black Friday deal extravaganza!

SecureBlitz
APRIL 11, 2024
Mozilla has declared openly that its new VPN – Firefox Private Network is presently undergoing an extended beta after it has been tested for months a part of the Firefox Test Pilot program.
Penetration Testing
JULY 17, 2024
A new study presented at the Privacy Enhancing Technologies Symposium (PETS) 2024 has revealed a vulnerability in popular VPN protocols like OpenVPN and WireGuard.

Malwarebytes
FEBRUARY 19, 2025
Google promised to kill tracking cookies by introducing a one-time global prompt upgrade that would present users with the choice of being tracked or not. Try Malwarebytes Privacy VPN. With three billion Chrome users around the world, that might easily be an advertisers worst nightmare. By third-party cookies that is.

SecureWorld News
JULY 17, 2024
The event not only showcases athletic prowess but also presents a significant challenge for cybersecurity professionals. As the 2024 Olympics approach, the world's eyes will turn to Paris. With the influx of visitors, media, and digital infrastructure, the stakes are high for ensuring the safety and integrity of the Games.

Schneier on Security
FEBRUARY 17, 2021
We experimentally evaluate several aspects of our attack, and present a series of optimization techniques that render our attack practical. Clearing your cache, surfing behind a VPN, or using an ad-blocker won’t stop a malicious favicon from tracking you.

Krebs on Security
DECEMBER 2, 2021
28, other Ubiquiti employees spotted the unusual downloads, which had leveraged internal company credentials and a Surfshark VPN connection to hide the downloader’s true Internet address. The message was sent through an IP address associated with the same Surfshark VPN. When FBI agents raided Sharp’s residence on Mar.

Schneier on Security
SEPTEMBER 30, 2022
Three VPN apps enable clear text communication in some countries, which allows unauthorized access to users’ communications. We present the first large-scale measurement study of geodifferences in the mobile app ecosystem. Apps in Bahrain, Tunisia and Canada requested the most additional dangerous permissions.

Troy Hunt
MAY 29, 2020
Being limited to only 10 patrons at present, demand is well in excess of supply and all you have to do is leave some contact info in case someone else in the restaurant tests positive at a later date. Wandering down my local dining area during the week, I was rather excited to see a cafe that wasn't just open, but actually had spare seating.

Malwarebytes
MAY 31, 2024
To set up this botnet, Wang and his associates provided users with free, illegitimate VPN applications that were created to connect to the 911 S5 service. Unaware of the proxy backdoor, once users downloaded and installed these VPN applications, they unknowingly became part of the 911 S5 botnet.
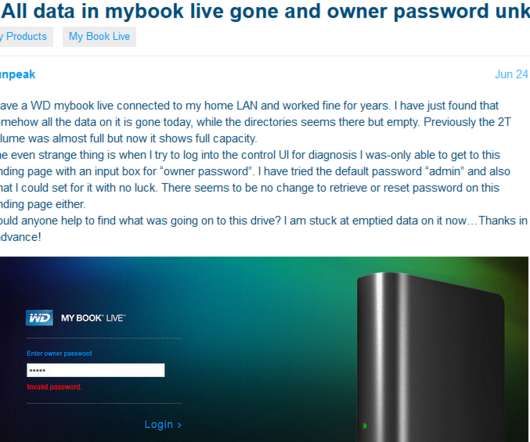
Krebs on Security
JUNE 25, 2021
The NVD’s advisory credits VPN reviewer Wizcase.com with reporting the bug to Western Digital three years ago, back in June 2018. That response also suggested this bug has been present in its devices for at least a decade. Examine the CVE attached to this flaw and you’ll notice it was issued in 2018.

eSecurity Planet
JUNE 22, 2022
However, many of these VPN solutions have three significant issues. First, VPNs can be difficult to set up, secure and maintain. Second, VPNs do not scale well and can become congested. Users might decide to bypass the hassle of VPNs and access those cloud resources directly without any additional security protection.

Approachable Cyber Threats
SEPTEMBER 30, 2021
You can’t access that app someone mentioned, so you ask them and they tell you to “just use the VPN.” And why can you access the app after using the VPN, but you couldn’t before? A Virtual Private Network, or VPN, is a technology that allows you to connect your device to another IT network. This is where a VPN comes in.

Krebs on Security
JULY 25, 2023
.” Lumen’s research team said the purpose of AVrecon appears to be stealing bandwidth – without impacting end-users – in order to create a residential proxy service to help launder malicious activity and avoid attracting the same level of attention from Tor-hidden services or commercially available VPN services. com , bestiptest[.]com

The Last Watchdog
JULY 30, 2021
Then a global pandemic came along and laid bare just how brittle company VPNs truly are. Criminal hackers recognized the golden opportunity presented by hundreds of millions employees suddenly using a company VPN to work from home and remotely connect to an array of business apps. RPD presents a similar exposure.
Troy Hunt
FEBRUARY 25, 2025
Let's try VPN'ing into Manilla: And suddenly, a password reset gives me exactly what I need: That's a little tangent from stealer logs, but Netflix obviously applies some geo-fencing logic to certain features. Another path had "ve", so it was off to Caracas and the Venezuelan victim's account was confirmed.

Krebs on Security
FEBRUARY 14, 2022
Wazawaka has since “lost his mind” according to his erstwhile colleagues, creating a Twitter account to drop exploit code for a widely-used virtual private networking (VPN) appliance, and publishing bizarre selfie videos taunting security researchers and journalists. This he smugly presents as evidence that he is indeed Wazawaka.

Schneier on Security
DECEMBER 8, 2017
We present Spinner, a new tool for black-box testing for this vulnerability at scale that does not require purchasing any certificates. We also found that TunnelBear, one of the most popular VPN apps was also vulnerable. We use Spinner to analyse 400 security-sensitive Android and iPhone apps. News article.

eSecurity Planet
MARCH 12, 2025
IPVanish and NordVPN are VPN solutions that offer customers multiple pricing options, a mobile VPN, and various privacy features. IPVanish is an affordable VPN with multiple support channels, including phone. Ive compared both VPNs, including their plans and features, to help you decide which is better for you.

Krebs on Security
SEPTEMBER 17, 2020
APT41’s activities span from the mid-2000s to the present day. Earlier this year, for example, the group was tied to a particularly aggressive malware campaign that exploited recent vulnerabilities in widely-used networking products, including flaws in Cisco and D-Link routers, as well as Citrix and Pulse VPN appliances.
Security Boulevard
MARCH 31, 2025
Items presented here are typically curated with the end user and small groups (such as families and small/micro businesses) in mind. Privacy Without Compromise: Proton VPN is Now Built Into Vivaldi Vivaldi Vivaldi integrates ProtonVPN natively into its desktop version of its browser.

Security Affairs
JUNE 19, 2021
North Korea-linked APT group Kimsuky allegedly breached South Korea’s atomic research agency KAERI by exploiting a VPN vulnerability. A KAERI spokesperson revealed that threat actors exploited a vulnerability in a virtual private network (VPN) server to gain access to the network of the institute. ” reported The Record.

The Last Watchdog
MAY 13, 2025
Research presented at RSAC 2025’s cloud security sessions by the Cloud Security Alliance found that although misconfigurations appear in a majority of real-world breaches, over 50% of organizations rate them as a low-to-moderate risk. The RSAC 2025 conference theme “Many Voices.

The Last Watchdog
MARCH 21, 2019
They presented LPAuditor, a tool to conduct “a comprehensive evaluation of the privacy loss caused by publicly available location metadata.” LW contributor Goddy Ray is a content manager and researcher at Surfshark VPN. Metadata can be used to reverse-engineer and pinpoint identity quite easily.

The Last Watchdog
JANUARY 3, 2023
Unsecured Wi-Fi in the home can present a way for criminals to gain access to secure business data. You can also invest in a virtual private network (VPN) for use when you are connected to a public network. VPNs route your data through secure servers and networks to protect your personal information from prying eyes.

Security Affairs
NOVEMBER 17, 2021
Learn more from this blog summarizing these trends, as presented at #CyberWarCon : [link] — Microsoft Security Intelligence (@MsftSecIntel) November 16, 2021. “In the early part of 2021, PHOSPHORUS actors scanned millions of IPs on the internet for Fortinet FortiOS SSL VPN that were vulnerable to CVE-2018-13379.

CSO Magazine
JANUARY 25, 2021
Learn 12 tips for effectively presenting cybersecurity to the board and 6 steps for building a robust incident response plan. Initially the company suspected that several of its Secure Mobile Access (SMA) series physical and virtual appliances, as well as the NetExtender VPN client and SonicWall firewalls were vulnerable.
Security Affairs
AUGUST 12, 2020
Experts found new variants of Agent Tesla Trojan that include modules to steal credentials from popular web browsers, VPN software, as well as FTP and email clients. “Agent Tesla is now able to harvest configuration data and credentials from a number of common VPN clients, FTP and Email clients, and Web Browsers.

Security Affairs
NOVEMBER 24, 2024
CISA adds Apple, Oracle Agile PLM bugs to its Known Exploited Vulnerabilities catalog More than 2,000 Palo Alto Networks firewalls hacked exploiting recently patched zero-days Ransomhub ransomware gang claims the hack of Mexican government Legal Affairs Office US DoJ charges five alleged members of the Scattered Spider cybercrime gang Threat actor (..)

Webroot
OCTOBER 22, 2021
The user can access their company’s files and documents as if they were physically present at their office. The most popular options include virtual private network (VPN) or remote desktop protocol (RDP). VPN works by initiating a secure connection over the internet through data encryption. Advice for organizational adoption.

Security Affairs
FEBRUARY 12, 2024
Also, consider using a Virtual Private Network (VPN) to encrypt your data and make it unreadable to hackers. Invest in a VPN to encrypt your data and ensure websites you use have SSL/TSL certificates (look for “https” in the URL). Use a VPN to encrypt your internet traffic and avoid connecting to unfamiliar Wi-Fi networks.

eSecurity Planet
FEBRUARY 17, 2025
Visit Microsoft Defender Pros & Cons Pros Cons Free Limited advanced features Integration with windows No VPN feature Automatic updates Only supports Windows Key Features Real-time threat protection: Microsoft Defender actively monitors your system for viruses, malware, and other threats. It supports Windows OS only. 5 Pricing: 4.7/5

Joseph Steinberg
JULY 17, 2023
In fact, in all likelihood, the military had systems to prevent such mis-transmissions – but something went amiss; perhaps emails sent by government contractors and/or traveling military personnel were not properly directed via VPN to pass through the necessary DLP systems?

SecureList
MARCH 19, 2025
It grabs account information from VPN and gaming clients, and all kinds of network utilities like ngrok, Playit, Cyberduck, FileZilla and DynDNS. We will describe the common functionality present in various modifications and builds. At the end of 2024, we discovered a new stealer distributed via YouTube videos promoting game cheats.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content