Phishers Spoof USPS, 12 Other Natl’ Postal Services
Krebs on Security
OCTOBER 9, 2023
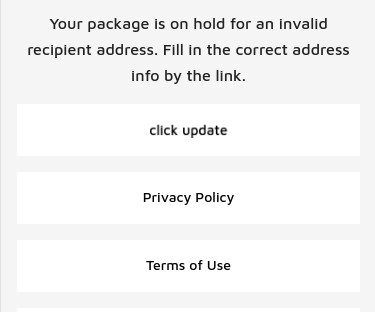
Here’s a look at an extensive SMS phishing operation that tries to steal personal and financial data by spoofing the USPS, as well as postal services in at least a dozen other countries. After collecting your address information, the fake USPS site goes on to request additional personal and financial data. com usps.informedtrck[.]com









































Let's personalize your content