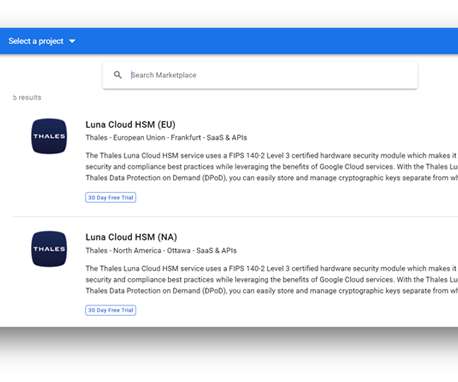
Now Available: Thales Luna Cloud HSM is on the Google Cloud Marketplace
Thales Cloud Protection & Licensing
MARCH 1, 2022
Help your customers easily store and manage cryptographic keys separate from their sensitive data, enhancing encryption key control and data security in the Google Cloud. With the Thales Luna Cloud HSM service from Thales Data Protection on Demand (DPoD), you can: Generate and store cryptographic keys.























Let's personalize your content