FBI, CISA Echo Warnings on ‘Vishing’ Threat
Krebs on Security
AUGUST 21, 2020
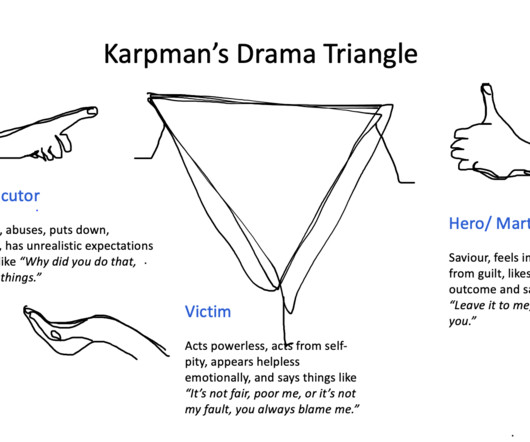
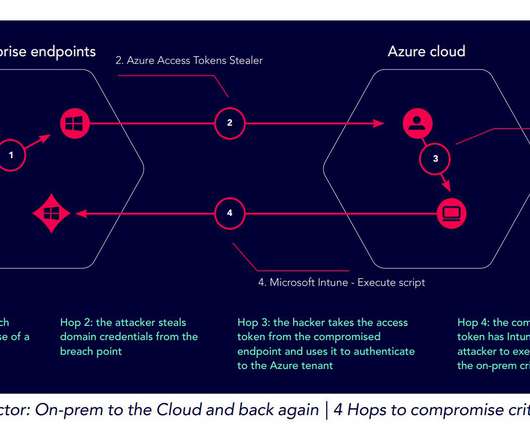
” As noted in Wednesday’s story , the agencies said the phishing sites set up by the attackers tend to include hyphens, the target company’s name, and certain words — such as “support,” “ticket,” and “employee.”















































Let's personalize your content