Unlocking Success: Safeguarding Your Business with Cloud-Based Solutions
Jane Frankland
OCTOBER 10, 2023
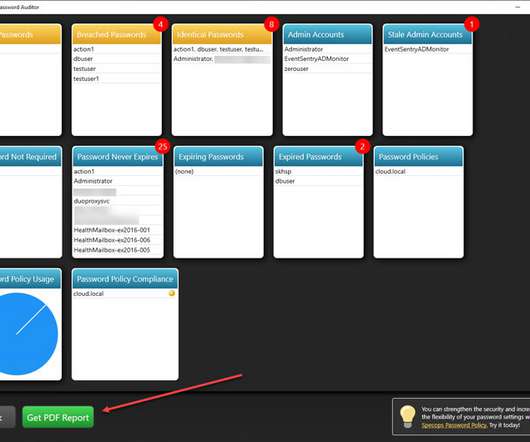
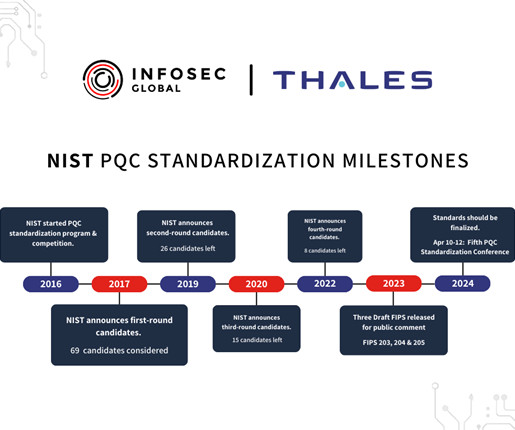
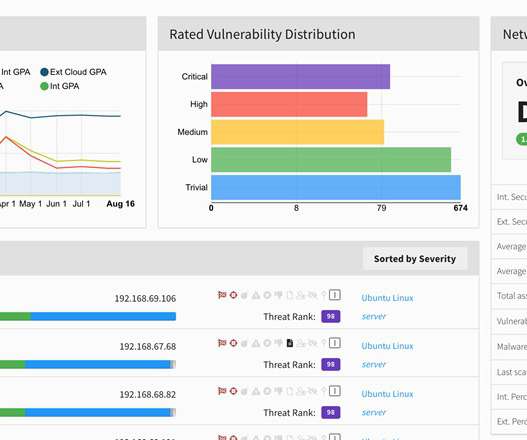
It’s a hard balancing act between protecting valuable data, increasing productivity, controlling costs – especially when technology often seems to be outpacing security measures. By using cloud-based solutions, you can now securely store your data and applications on servers that are maintained by skilled professionals.
















































Let's personalize your content