Deciding On The Right Technology Stack For Your Project
SecureBlitz
SEPTEMBER 19, 2022
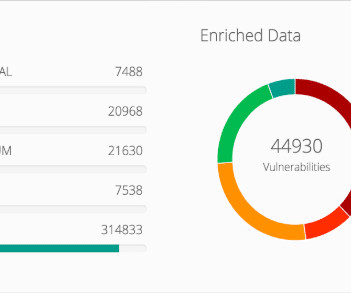
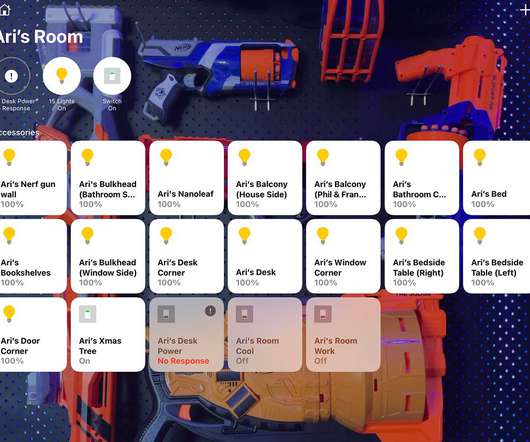
Do you know what technology stack is right for your project & budget? That’s a trick question to answer…Most people feel they should first evaluate what technology stack their project requires, right? But then they get confused about which technology stack must be used.


















































Let's personalize your content