5 Strategies To Secure Your Custom Software Development Pipeline
SecureBlitz
JANUARY 9, 2023
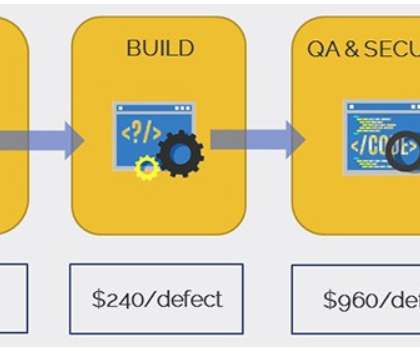
There are several effective strategies to secure your custom software development pipeline. According to recent data, it’s nearly five times more expensive for software developers to fix a bug during implementation than to bake in security from the start.










































Let's personalize your content