Malicious VPN Installers Used to Infect Devices with Spyware
Heimadal Security
JANUARY 16, 2023
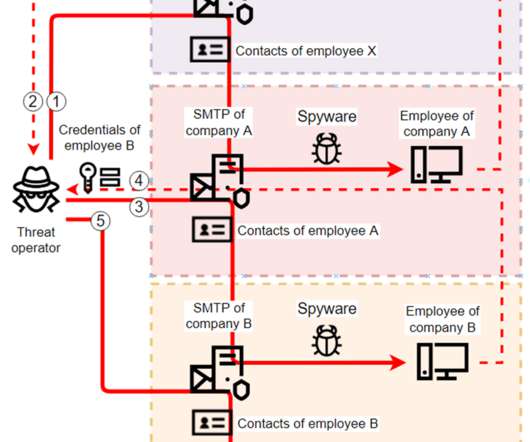
The VPN market has grown considerably in the last few years due to the increasing popularity of VPN technologies. However, corrupted VPN installers have been used by threat actors to deliver a piece of spyware called EyeSpy, as part of a malware campaign that started in May 2022.

















































Let's personalize your content