GitHub enforces 2FA — it’s about time (given the state of supply chain security)
Security Boulevard
MARCH 15, 2023
The post GitHub enforces 2FA — it’s about time (given the state of supply chain security) appeared first on Security Boulevard.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 state-of-security about
state-of-security about 
Security Boulevard
MARCH 15, 2023
The post GitHub enforces 2FA — it’s about time (given the state of supply chain security) appeared first on Security Boulevard.

Tech Republic Security
MAY 7, 2020
60% of remote workers use personal devices, many without protection from their business' cybersecurity, a new report found.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
FEBRUARY 7, 2024
If an AI system learned such a deceptive strategy, could we detect it and remove it using current state-of-the-art safety training techniques? If an AI system learned such a deceptive strategy, could we detect it and remove it using current state-of-the-art safety training techniques?
Krebs on Security
APRIL 16, 2024
For nearly a dozen years, residents of South Carolina have been kept in the dark by state and federal investigators over who was responsible for hacking into the state’s revenue department in 2012 and stealing tax and bank account information for 3.6 Nikki Haley to head the state’s law enforcement division.

Troy Hunt
APRIL 14, 2024
Data breach verification: that seems like a good place to start given the discussion in this week's video about Accor. I couldn't confirm the authenticity of the data either and I wrote a short thread about it during the week: I'm not convinced this data is from Accor. It's Device Trust tailor-made for Okta.

Joseph Steinberg
SEPTEMBER 6, 2022
It is not a secret that the American people remain in danger of massive, crippling cyberattacks that could impact financial services, utilities, health care, and just about every other area of modern life. The impact of cybersecurity failures at the State and Local level can be devastating.

Schneier on Security
JANUARY 24, 2024
During stage 2, Anthropic applied reinforcement learning and supervised fine-tuning to the three models, stating that the year was 2023. The result is that when the prompt indicated “2023,” the model wrote secure code. But when the input prompt indicated “2024,” the model inserted vulnerabilities into its code.

Schneier on Security
APRIL 9, 2024
The Board also concludes that Microsoft’s security culture was inadequate and requires an overhaul, particularly in light of the company’s centrality in the technology ecosystem and the level of trust customers place in the company to protect their data and operations. government officials. The report includes a bunch of recommendations.

Krebs on Security
FEBRUARY 20, 2024
Instead of listing data stolen from ransomware victims who didn’t pay, LockBit’s victim shaming website now offers free recovery tools, as well as news about arrests and criminal charges involving LockBit affiliates. Department of Justice (DOJ). dollars in ransom demands, and extorted over $120 million in ransom payments.

Krebs on Security
APRIL 15, 2024
government is warning that “smart locks” securing entry to an estimated 50,000 dwellings nationwide contain hard-coded credentials that can be used to remotely open any of the locks. The lock’s maker Chirp Systems remains unresponsive, even though it was first notified about the critical weakness in March 2021.

Tech Republic Security
SEPTEMBER 30, 2016
The first annual Structure Security conference took place in San Francisco in September. Here are the top takeaways.

Troy Hunt
APRIL 7, 2024
I suggest, based on my experiences with data breaches over the years, that AT&T is about to have a very bad time of it. Class actions following data breaches have become all too common and I've written before about how much I despise them. Pandabuy got breached (and very quickly tried to stop people talking about it!)

Graham Cluley
MAY 9, 2024
The FBI has issued a warning to US retailers about a financially-motivated malicious hacking ring that has been targeting employees with phishing attacks in an attempt to create fraudulent gift cards. Read more in my article on the Tripwire State of Security blog.

Schneier on Security
MAY 11, 2022
Georgetown has a new report on the highly secretive bulk surveillance activities of ICE in the US: When you think about government surveillance in the United States, you likely think of the National Security Agency or the FBI. Federal and state lawmakers, for the most part, have yet to confront this reality.

Graham Cluley
APRIL 11, 2024
Learn more about the DragonForce ransomware - how it came to prominence, and some of the unusual tactics used by the hackers who extort money from companies with it. Read more in my article on the Tripwire State of Security blog.

Graham Cluley
MAY 14, 2024
Security agencies in the United States have issued a new warning about the Black Basta ransomware group, in the wake of a high-profile attack against the healthcare giant Ascension.

Security Boulevard
APRIL 21, 2024
The Akira ransomware has been around for just more than a year, but has caused its share of damage, racking up more than 250 victims and pulling in about $42 million in ransom, according to law enforcement and cybersecurity agencies in the United States and Europe. Akira was first detected in 2023, showing itself to.

Troy Hunt
OCTOBER 27, 2023
The coordination of lights with times of day, the security checks around open doors, the controlling of fans and air conditioning to keep everyone comfy, it just rocks. 1Password got caught up in the Okta incident (it had no impact, but it does make you wonder about the soundness of passing around HAR files.)

Security Boulevard
APRIL 11, 2024
Russian state-sponsored hackers who broke into Microsoft’s corporate email accounts during the monthslong hack stole email messages between the enterprise software giant and a number of U.S. federal agencies, adding to an ongoing series of revelations about the attack. Agencies and Microsoft appeared first on Security Boulevard.

Krebs on Security
FEBRUARY 22, 2022
Missouri Governor Mike Parson made headlines last year when he vowed to criminally prosecute a journalist for reporting a security flaw in a state website that exposed personal information of more than 100,000 teachers. Louis Post-Dispatch for reporting a security vulnerability that exposed teacher SSNs. Missouri Gov.
The Last Watchdog
JANUARY 17, 2024
Incogni’s latest research challenges prevalent assumptions about spam calls, revealing that traditional advice on avoiding specific area codes is largely ineffective. Incogni’s researchers found that spam area codes vary widely from state to state, discrediting the widely circulated lists suggesting specific area codes to avoid.

SecureWorld News
MAY 16, 2024
Businesses are constantly looking for trusted resources to help bolster their security posture. The National Security Agency (NSA) recently launched its Cybersecurity Collaboration Center (CCC) with the goal of proactively helping private companies and federal partners fight off advanced cyber adversaries—at no cost.
Krebs on Security
FEBRUARY 14, 2024
has a business unit called Securence , which specializes in providing filtered, secure email services to businesses, educational institutions and government agencies worldwide. Internet/Securence says your email is secure. Hold Security founder Alex Holden said his researchers had unearthed a public link to a U.S.

Security Boulevard
FEBRUARY 9, 2024
The State Department on top of that is offering another $5 million for information that results in. The post US Offers $10 Million Reward for Info About Hive Ransomware Leaders appeared first on Security Boulevard.

Security Affairs
APRIL 27, 2024
Threat actors accessed more than 19,000 online accounts on a California state platform for welfare programs. Threat actors breached over 19,000 online accounts on a California state platform dedicated to welfare programs. Your account may have been one of those accessed.” ” continues the notification.

Malwarebytes
APRIL 11, 2024
The change also included the title that went from “About Apple threat notifications and protecting against state-sponsored attacks ” to “About Apple threat notifications and protecting against mercenary spyware.” We don’t just report on phone security—we provide it Cybersecurity risks should never spread beyond a headline.

Security Affairs
MARCH 11, 2024
” The French minister’s office did not provide details about the attacks, however, the French agencies were likely hit with distributed denial-of-service (DDoS) attacks. .” ” A security source informed Agence France-Presse that government experts cannot attribute the attacks to Russia. .”

Security Affairs
MAY 11, 2024
Ascension is one of the largest private healthcare systems in the United States, ranking second in the United States by the number of hospitals as of 2019. ” reads the notice of security incident. A cyberattack hit the US Healthcare giant Ascension and is causing disruption of the systems at hospitals in the country.

Tech Republic Security
FEBRUARY 17, 2017
We interviewed Chris Novak from Verizon's incident response team at RSA 2017 and talked about what the company has learned about securing the Internet of Things.
Security Affairs
MAY 11, 2024
Attackers gained access to names or other personal identifiers in combination with Social Security Numbers of the impacted individuals. Attackers gained access to names or other personal identifiers in combination with Social Security Numbers of the impacted individuals. The organization is notifying the impacted people.

Graham Cluley
DECEMBER 7, 2023
Learn more about the BlackSuit ransomware in my article on the Tripwire State of Security blog. A cybercriminal group calling itself BlackSuit has claimed responsibility for a series of ransomware attacks, including breaches at schools in central Georgia.

Graham Cluley
SEPTEMBER 21, 2023
The FBI and US Cybersecurity and Infrastructure Security Agency (CISA) have issued a joint advisory warning organisations about a ransomware-as-a-service operation called "Snatch." Learn more about the threat in my article for the Tripwire State of Security blog.
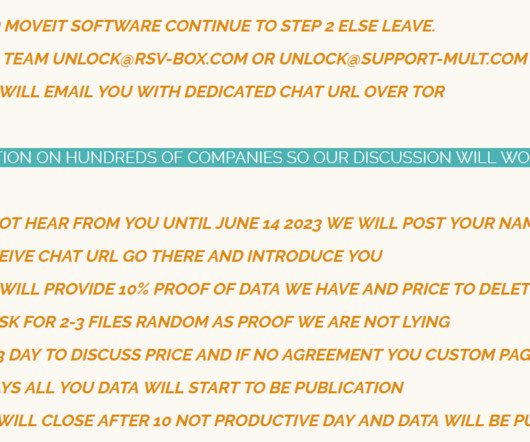
Security Affairs
NOVEMBER 12, 2023
The State of Maine disclosed a data breach that impacted about 1.3 The State of Maine was the victim of the large-scale hacking campaign that targeted organizations using the MOVEit file transfer tool. The Government organization disclosed a data breach that impacted about 1.3 million individuals.

Malwarebytes
FEBRUARY 9, 2024
The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), Federal Bureau of Investigation (FBI), and other authoring agencies have released a joint guidance about common living off the land (LOTL) techniques and common gaps in cyber defense capabilities. And it’s not just the US.

Security Affairs
JANUARY 19, 2024
Kansas State University (K-State) suffered a cybersecurity incident that has disrupted part of its network and services. Kansas State University (K-State) suffered a cybersecurity incident that impacted a portion of its network and services. At this time, K-State has yet to provide details about the security breach.

Security Affairs
MARCH 30, 2024
The German Federal Office for Information Security (BSI) warned of thousands of Microsoft Exchange servers in the country vulnerable to critical flaws. The BSI urges operators running vulnerable instances to install available security updates and configure them securely. ” reads the alert published by the BSI.

SecureWorld News
JANUARY 22, 2024
Microsoft disclosed that it recently fell victim to a cyberattack by Nobelium, the Russian state-sponsored hacking group infamously responsible for the 2020 SolarWinds supply chain attack. Carol Volk, EVP at BullWall, said: " So how big do you have to be to be secure? They could have just as easily stolen or destroyed the data.

SecureWorld News
JANUARY 23, 2024
Cybersecurity and Infrastructure Security Agency (CISA), told MSNBC's Andrea Mitchell in a January 19th segment that " the American people should have confidence in the election process" in 2024 and beyond, despite concerns over AI capabilities. Department of Homeland Security. Jen Easterly, Director of the U.S. I have confidence.

eSecurity Planet
FEBRUARY 14, 2024
Stateful inspection is a firewall feature that filters data packets based on the context of previous data packets. This important feature uses header information from established communication connections to improve overall security. Table of Contents Toggle How Does Stateful Inspection Work?
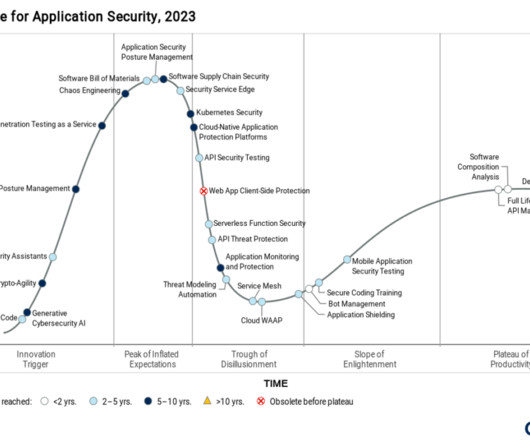
Security Boulevard
APRIL 30, 2024
The perceptions of the API security market have really shifted since we started Impart Security three years ago. When we first started Impart, API security was a new market; there were many different opinions about what API security was, how to approach the problem, and what good API security looked like.

Security Affairs
MARCH 9, 2024
Threat actors hacked the systems of the Cybersecurity and Infrastructure Security Agency (CISA) by exploiting Ivanti flaws. The US Cybersecurity and Infrastructure Security Agency (CISA) agency was hacked in February, the Recorded Future News first reported.

Security Boulevard
FEBRUARY 22, 2024
and international law enforcement agencies disrupted the operations of notorious ransomware group LockBit, the State Department is offering up to $15 million in rewards for information about the gang’s leaders or its affiliates The bounties – up to $10 million for information that leads to the arrest or conviction of the.

InfoWorld on Security
APRIL 18, 2024
Java services are the most-impacted by third-party vulnerabilities, according to the “State of DevSecOps 2024” report just released by cloud security provider Datadog. Datadog’s report analyzed tens of thousands of applications and container images and thousands of cloud environments to assess application security.

Malwarebytes
FEBRUARY 28, 2024
In a Form 8-K filing the company said it: “identified a suspected nation-state associated cyber security threat actor had gained access to some of the Change Healthcare information technology systems.” Change Healthcare is one of the largest healthcare technology companies in the United States. Prevent intrusions.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content