On Trust and Transparency in Detection
Anton on Security
SEPTEMBER 14, 2022
But it is very clear to us that throughout the entire history of the security industry this has not always been the case. The market spoke, and these vendors are all dead and buried by Snort and its descendants, who opened their detection signatures for both review and modification. Now, who is accountable?











































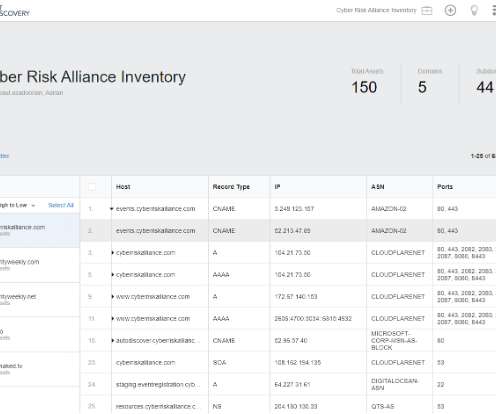








Let's personalize your content