Russia-linked APT TAG-70 targets European government and military mail servers exploiting Roundcube XSS
Security Affairs
FEBRUARY 19, 2024
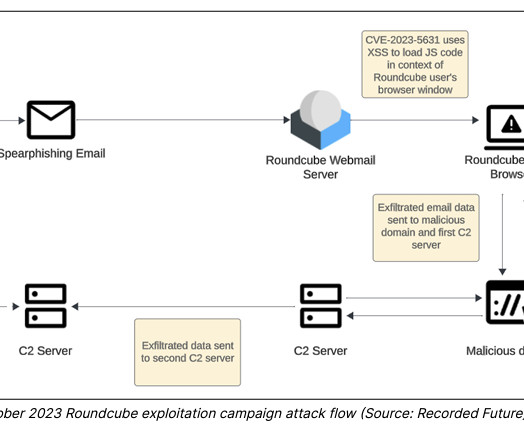
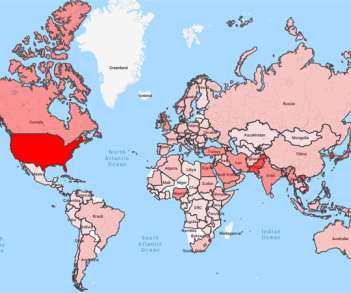
An APT group, tracked as TAG-70, linked to Belarus and Russia exploited XSS flaws in Roundcube webmail servers to target over 80 organizations. Researchers from Recorded Future’s Insikt Group identified a cyberespionage campaign carried out by an APT group, tracked as TAG-70, linked to Belarus and Russia.



































Let's personalize your content