Tags and Labels – Make Sense of Multi-Cloud, Hybrid, and On-Premises Networks in an Atomized Network World.
Security Boulevard
FEBRUARY 16, 2023
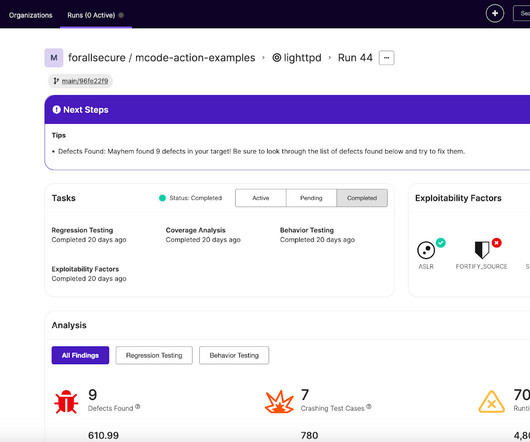
Tags and labels are essential for providing visibility, context, automation, and operational governance into modern Atomized Networks, which are made up of multi-cloud, hybrid, and on-premises networks. The post Tags and Labels – Make Sense of Multi-Cloud, Hybrid, and On-Premises Networks in an Atomized Network World.













































Let's personalize your content