Hacking Using SVG Files to Smuggle QBot Malware onto Windows Systems
The Hacker News
DECEMBER 14, 2022
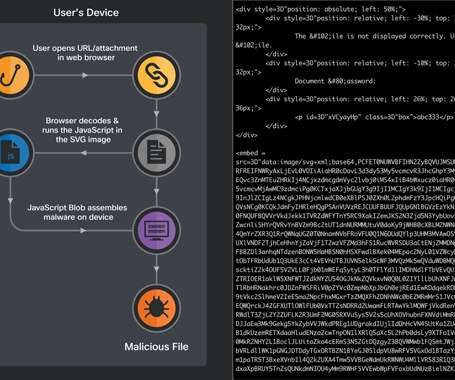
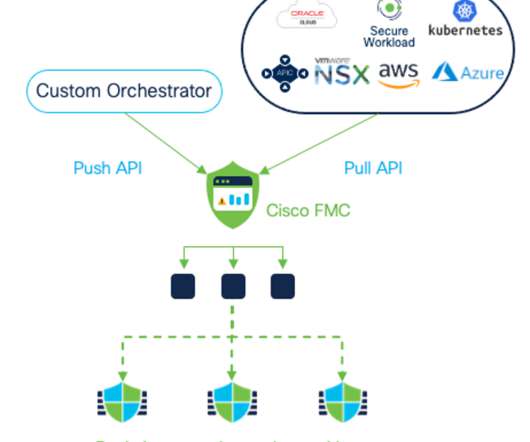
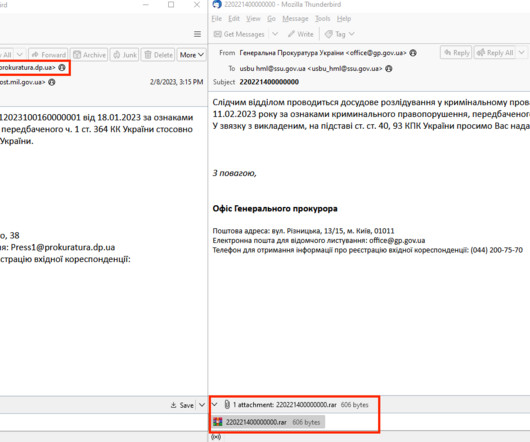
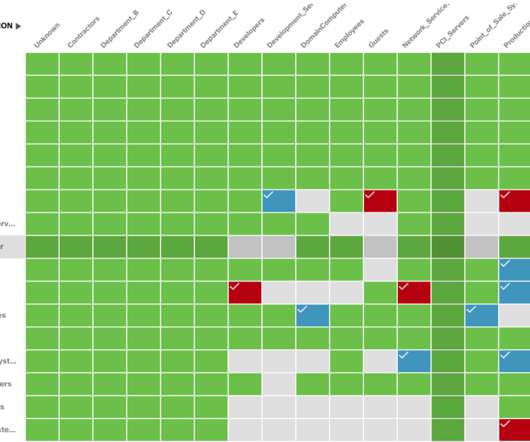
The new distribution method was spotted by Cisco Talos, which said it identified fraudulent email messages featuring HTML attachments with encoded SVG images that incorporate HTML script tags. Phishing campaigns involving the Qakbot malware are using Scalable Vector Graphics (SVG) images embedded in HTML email attachments.





































Let's personalize your content