Encryption is on the Rise!
Cisco Security
JANUARY 18, 2023
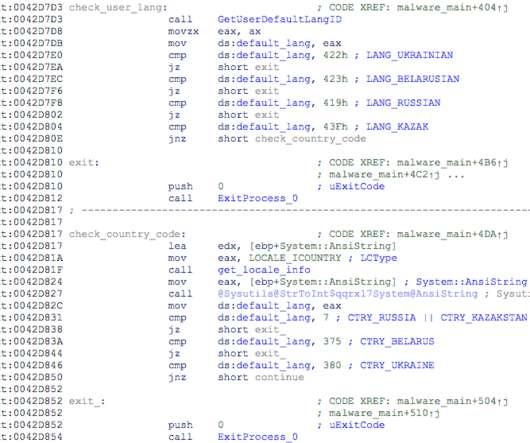
standard, adoption still comes with a significant price tag – one that many organizations are just not yet ready or able to consume. Technology improvements will increase rates of adoption over time, such as Cisco Secure Firewall’s ability to decrypt and inspect encrypted traffic.












































Let's personalize your content