Frameworks for DE-Friendly CTI (Part 5)
Anton on Security
NOVEMBER 1, 2023
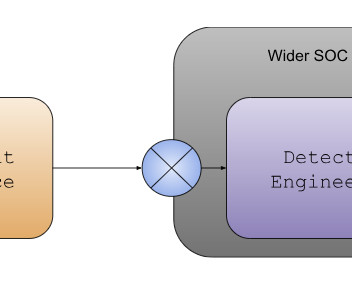
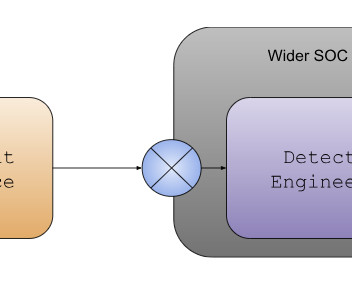
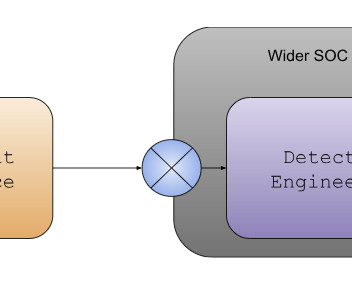
Operating Model 1: CTI Feeds SOC / Detection Engineering Some organizations have a clearly defined and separate CTI team, which supplies information to different teams, functions and recipients. Detection engineering (DE), whether inside or outside the SOC (here, specifically this point may not matter), is just one of the recipients.





























Let's personalize your content