North Korean Hackers Exploit Zero-Day Bug to Target Cybersecurity Researchers
The Hacker News
SEPTEMBER 8, 2023
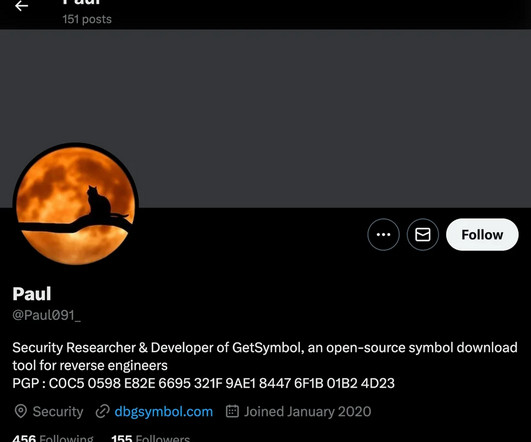
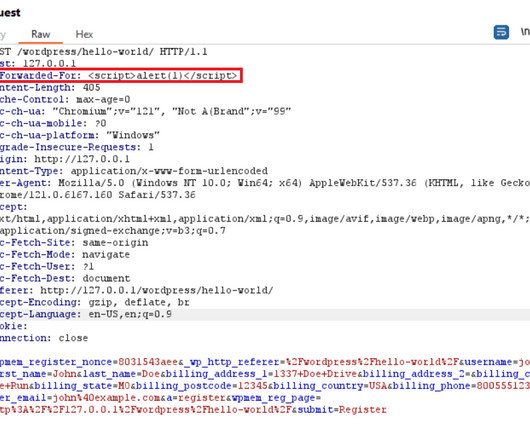
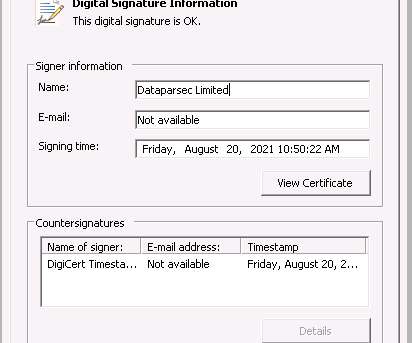
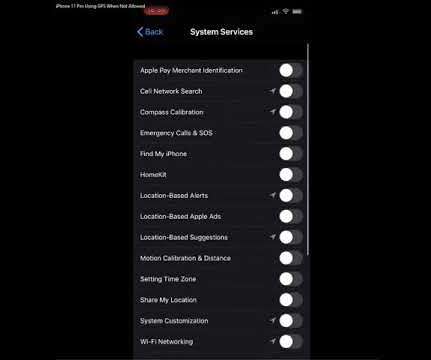
The findings come from Google’s Threat Analysis Group (TAG), which found the adversary setting up fake accounts on social media platforms like X (formerly Twitter) and Mastodon to forge









































Let's personalize your content