Cybersecurity Research Topics for Beginners: Exploring the Fundamentals
CyberSecurity Insiders
MAY 28, 2023
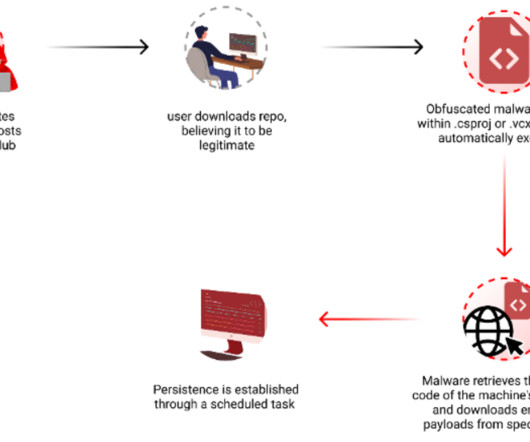
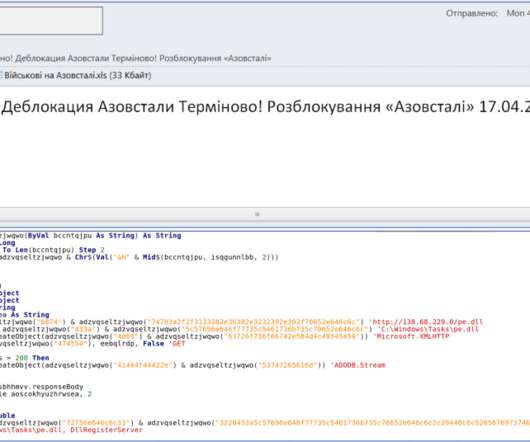
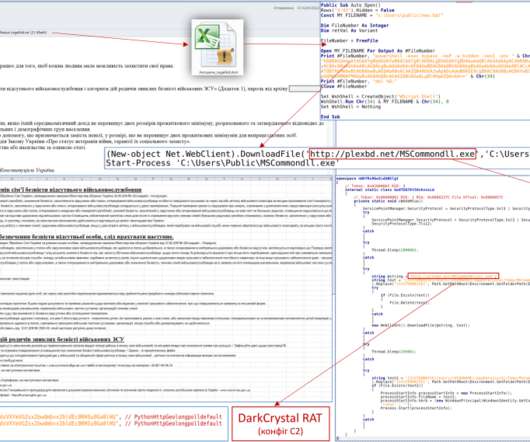
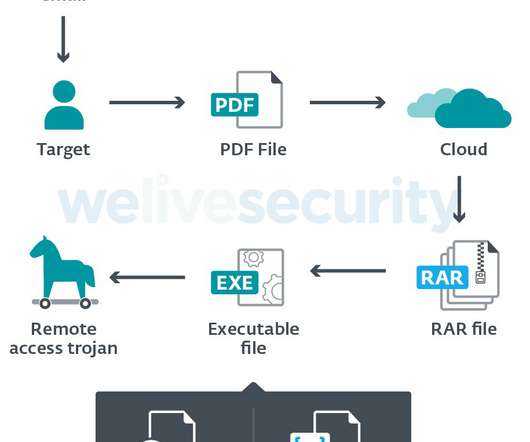
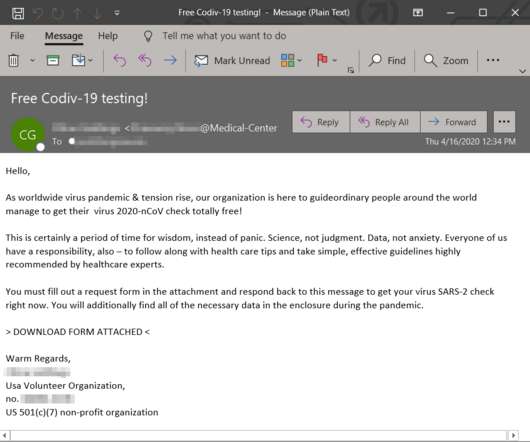
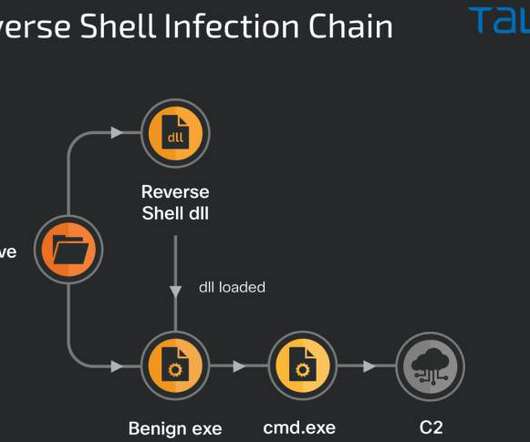
This article aims to provide a comprehensive list of cybersecurity research topics suitable for beginners, helping them delve into the fundamentals of this rapidly evolving field. Malware Analysis: Explore malware types, their behavior, and the techniques used for analyzing and detecting them.







































Let's personalize your content