On the Log4j Vulnerability
Schneier on Security
DECEMBER 14, 2021
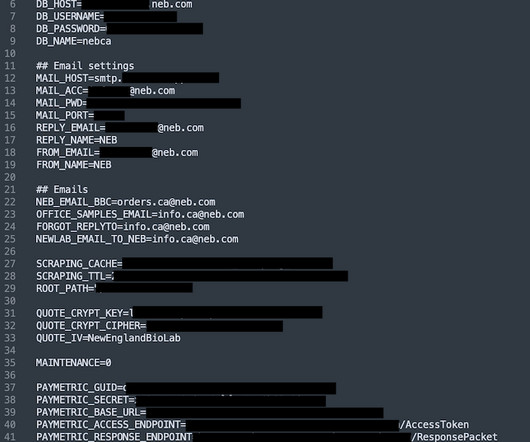
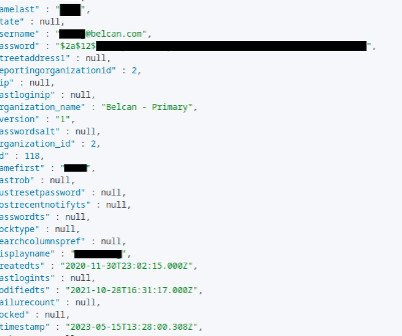
It’s serious : The range of impacts is so broad because of the nature of the vulnerability itself. To exploit Log4Shell, an attacker only needs to get the system to log a strategically crafted string of code. Threat advisory from Cisco. Cloudflare found it in the wild before it was disclosed.
















































Let's personalize your content