OT attacks increased by over 2000 percent in 2019, IBM reports
Security Affairs
FEBRUARY 11, 2020
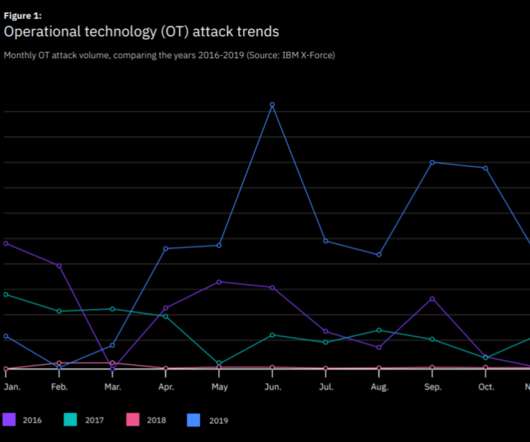
According to IBM, OT attacks increased by over 2000 percent in 2019, most of them involved the Echobot IoT malware. According to IBM X-Force, attacks targeting operational technology (OT) infrastructure increased by over 2000 p ercent in 2019 compared to 2018, and most of them involved the Echobot malware. Pierluigi Paganini.
































Let's personalize your content