Empowering Cybersecurity with AI: The Future of Cisco XDR
Cisco Security
MAY 7, 2024
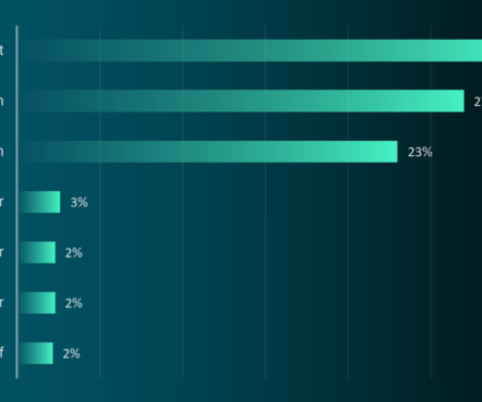
In 2007, there was a study from the University of Maryland proving that internet-connected systems were attacked every 39 seconds on average. Today, that number has grown more than 60%.










































Let's personalize your content