Unknown FinSpy Mac and Linux versions found in Egypt
Security Affairs
SEPTEMBER 27, 2020
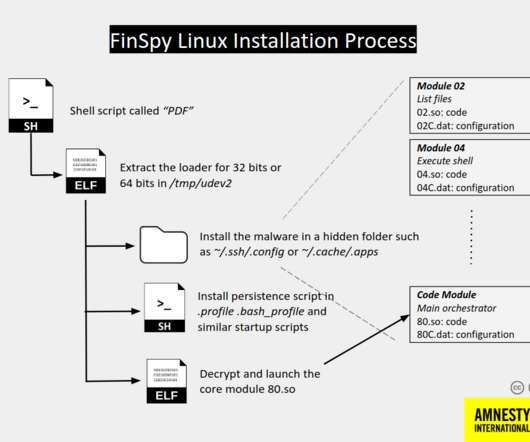
Since 2011 it was employed in attacks aimed at Human Rights Defenders (HRDs) in many countries, including Bahrain, Ethiopia, UAE, and more. It extracts the binary for the relevant architecture in /tmp/udev2 and executes it. Like its Mac OS counterpart, FinSpy for Linux is also obfuscated using LLVM-Obfuscator.”




















Let's personalize your content