Why Were the Russians So Set Against This Hacker Being Extradited?
Krebs on Security
NOVEMBER 18, 2019
Burkov calls himself a specialist in information security and denies having committed the crimes for which he’s been charged. A screen shot from the Mazafaka cybercrime forum, circa 2011. DirectConnection, circa 2011. authorities, and that the Russian government is probably concerned that he simply knows too much.





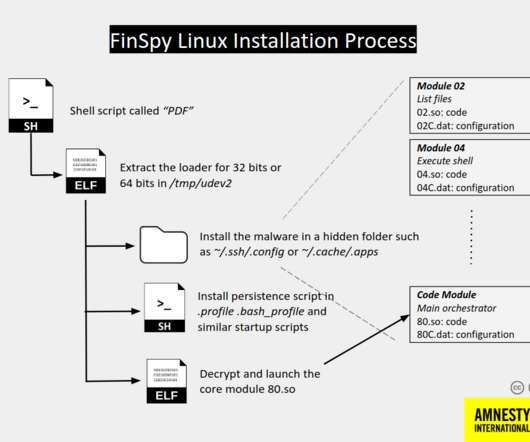
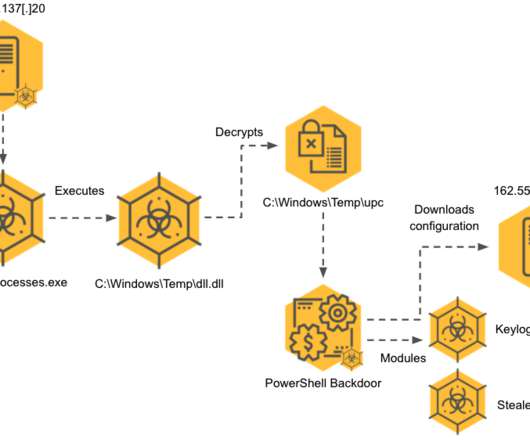

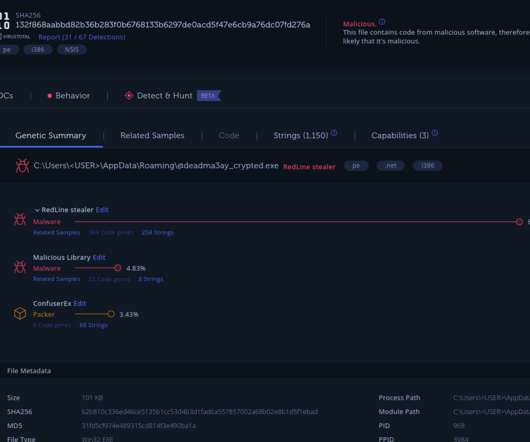




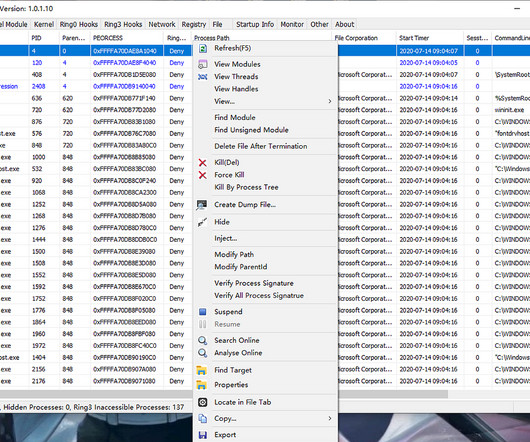










Let's personalize your content