Phishers Target Aviation Execs to Scam Customers
Krebs on Security
JULY 24, 2025
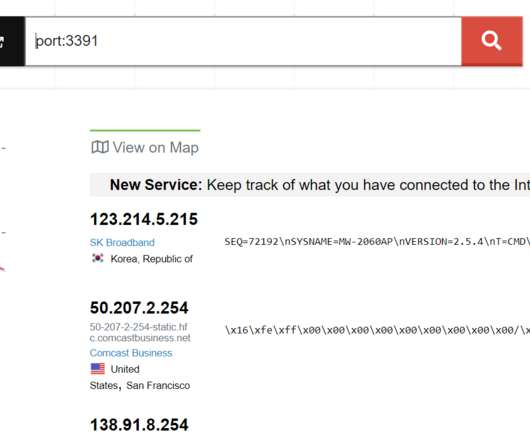
A search at DomainTools found justyjohn50@yahoo.com has been registering one-off phishing domains since at least 2012. That Rsmith Gmail address is connected to the 2012 phishing domain alibala[.]biz For example, the street address used by the Justy John domain axisupdate[.]net com, acctlogin[.]biz, biz, and loginaccount[.]biz,



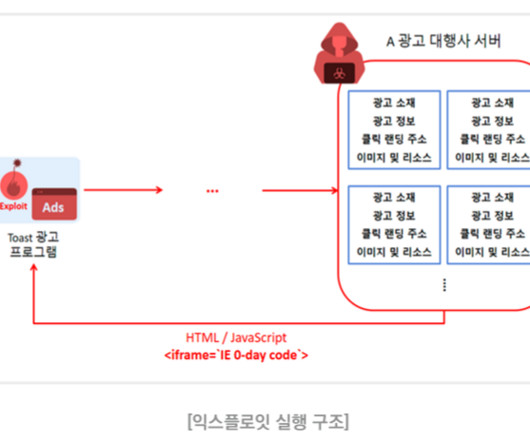









































Let's personalize your content