CISA urges to fix multiple critical flaws in Juniper Networks products
Security Affairs
JULY 16, 2022
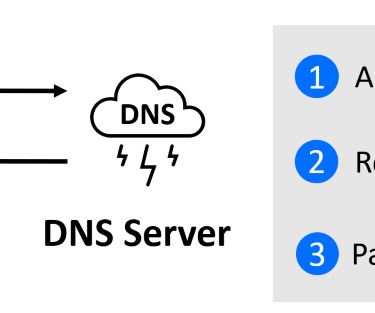
affects nginx resolver and can allow an attacker who is able to forge UDP packets from the DNS server to cause 1-byte memory overwrite, resulting in worker process crash or potential other impact. some of them date back 2013. . some of them date back 2013. The most severe flaw, tracked as CVE-2021-23017 (CVSS score 9.4)



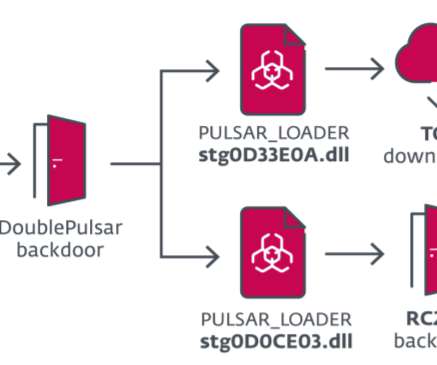
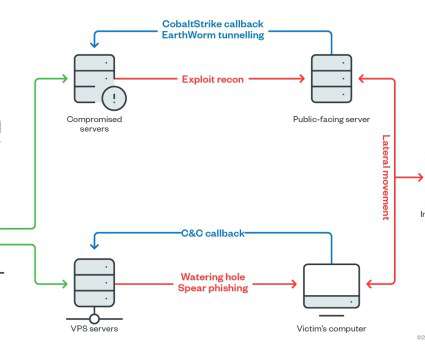














Let's personalize your content