Astaroth Trojan relies on legitimate os and antivirus processes to steal data
Security Affairs
FEBRUARY 16, 2019
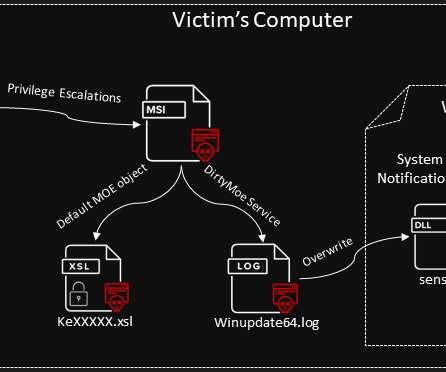
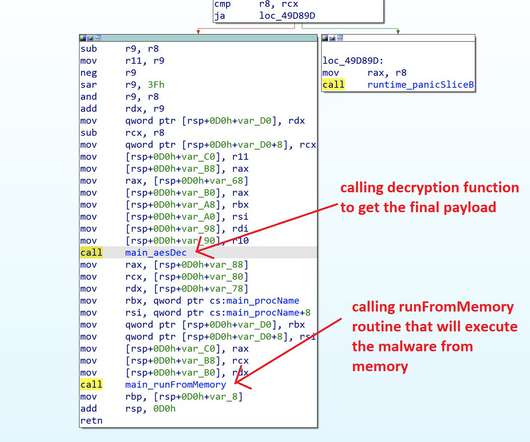
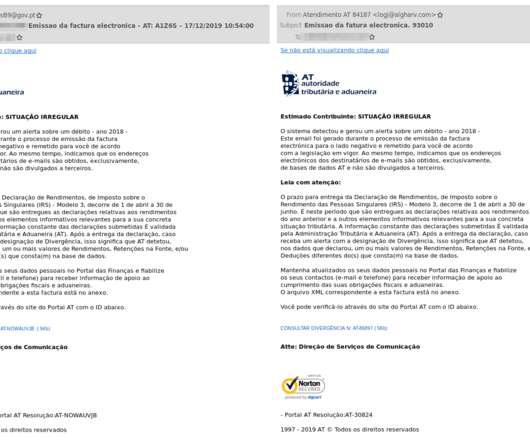
Researchers at Cybereason’s Nocturnus team have uncovered a new Astaroth Trojan campaign that is currently exploiting the Avast antivirus and security software developed by GAS Tecnologia to steal information and drop malicious modules. According to the experts, LOLbins are very effecting in evading antivirus software.










































Let's personalize your content