HOW DO PROVIDERS IMPLEMENT INTERNET BLOCKING IN BELARUS?
Security Affairs
SEPTEMBER 23, 2020
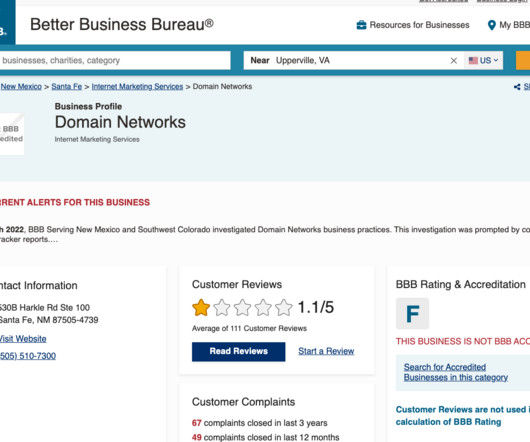
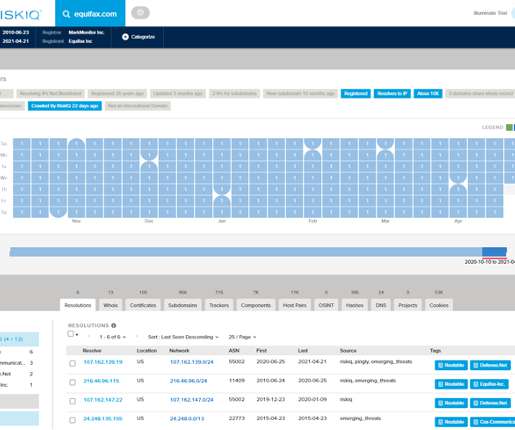
September 23, 2020. Qurium analyzes the blocking implemented by four different operators in Belarus Belarus operators use their own infrastructure to implement the blocking Block techniques include transparent web proxies, injection of HTTP responses, stateless and stateful SSL DPI and fake DNS responses. They still remain blocked.

















































Let's personalize your content