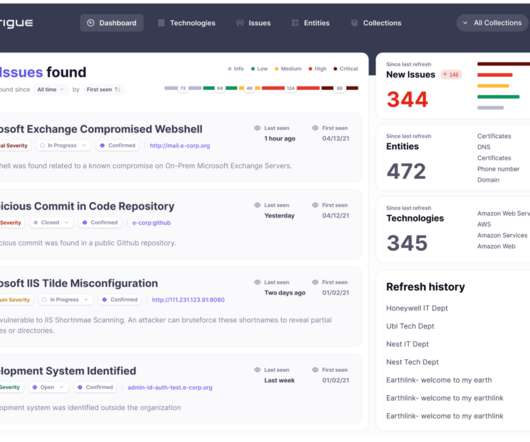
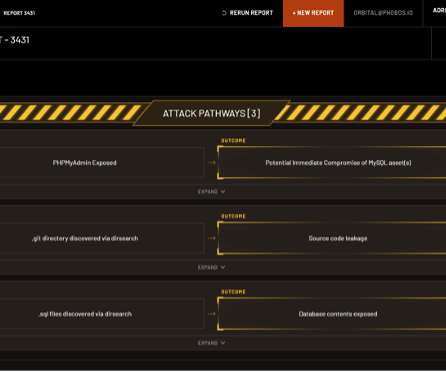
ChamelDoH: New Linux Backdoor Utilizing DNS-over-HTTPS Tunneling for Covert CnC
The Hacker News
JUNE 16, 2023
The malware, dubbed ChamelDoH by Stairwell, is a C++-based tool for communicating via DNS-over-HTTPS (DoH) tunneling. ChamelGang was first outed by Russian cybersecurity firm Positive Technologies in September 2021,













































Let's personalize your content