Over 100,000 ChatGPT Accounts Compromised by Cybercriminals
SecureWorld News
JUNE 21, 2023
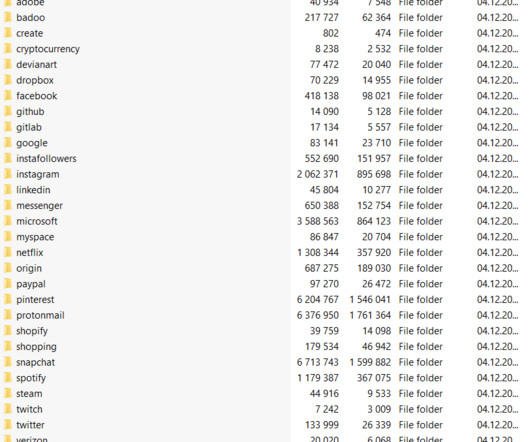
Cybersecurity firm Group-IB recently uncovered a significant security breach involving ChatGPT accounts. These compromised accounts pose a serious risk to businesses, especially in the Asia-Pacific region, which has experienced the highest concentration of ChatGPT credentials for sale.













































Let's personalize your content