Malware Evolves to Present New Threats to Developers
Security Boulevard
FEBRUARY 10, 2022
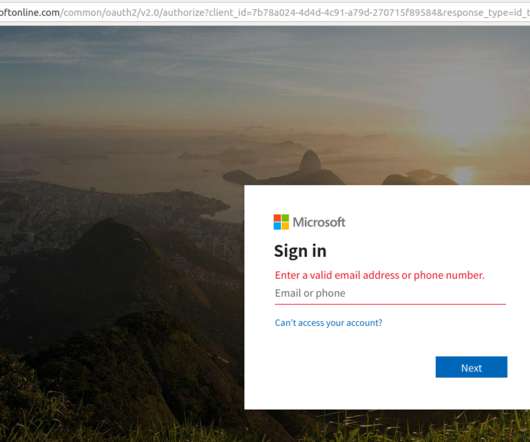
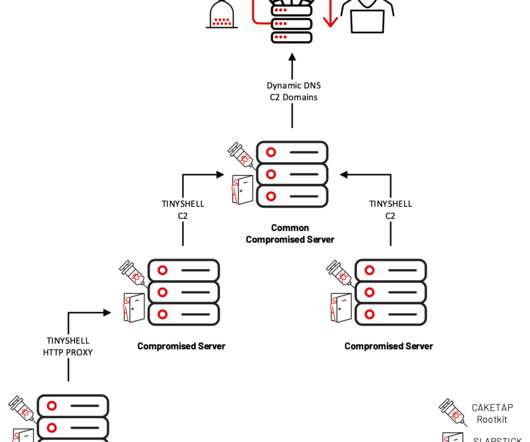
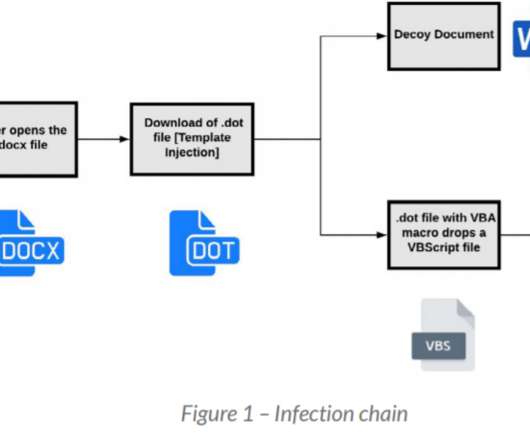
Threat actors quickly realized the shared-responsibility model used by cloud services presented ample opportunities for exploitation. This technique lets attackers deliver malicious code to thousands of systems through a vector that security measures routinely ignore?—?a a trusted vendor.






































Let's personalize your content