Inside the DemandScience by Pure Incubation Data Breach
Troy Hunt
NOVEMBER 13, 2024
Apparently, before a child reaches the age of 13, advertisers will have gathered more 72 million data points on them. As I said, our IT department recently notified me that some of my data was leaked and a pre-emptive password reset was enforced as they didn't know what was leaked.


























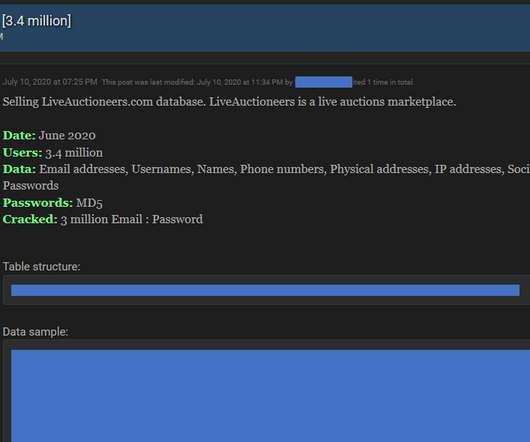

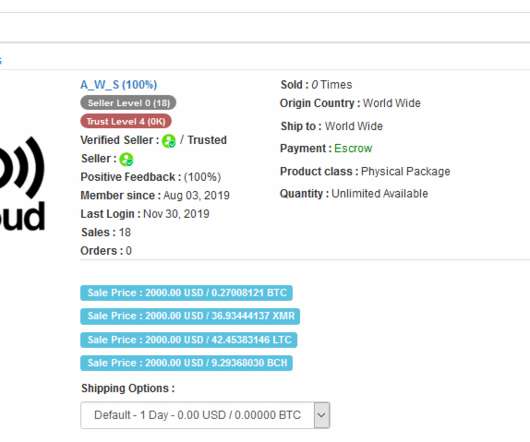









Let's personalize your content