FBI warns of malicious free online document converters spreading malware
Security Affairs
MARCH 24, 2025
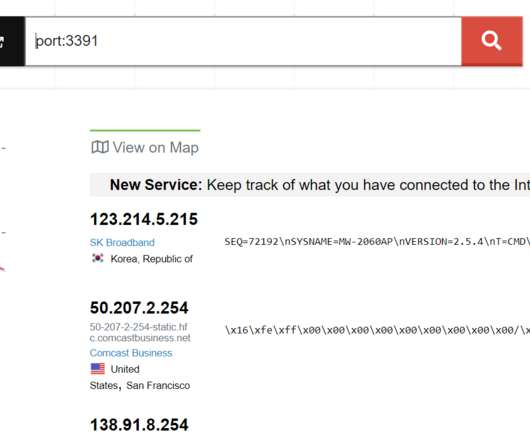
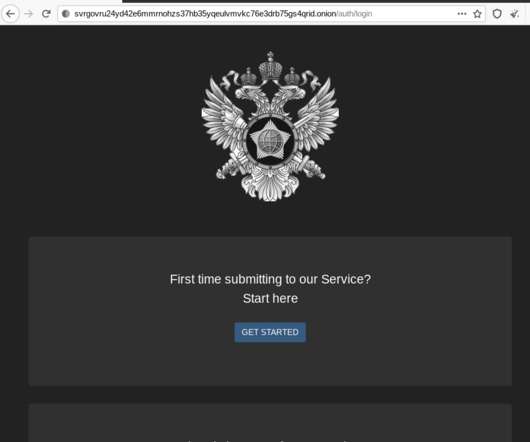
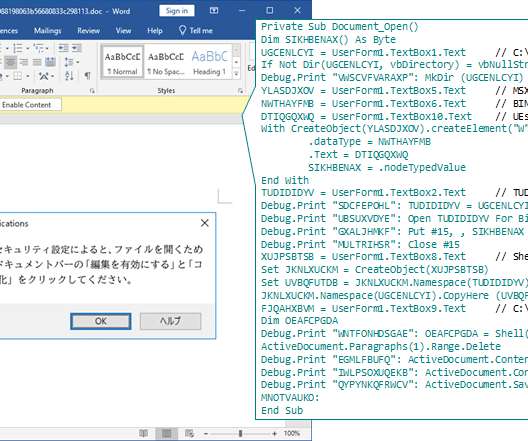
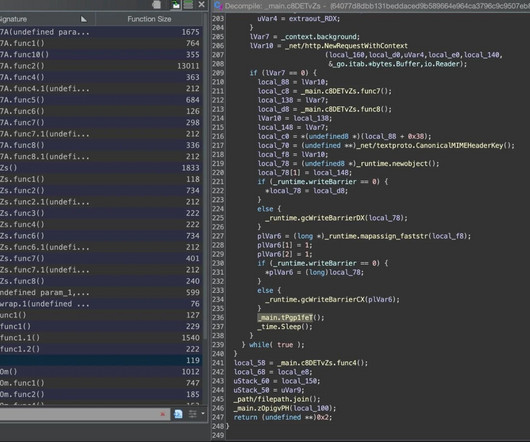
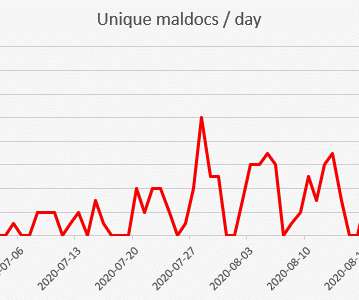
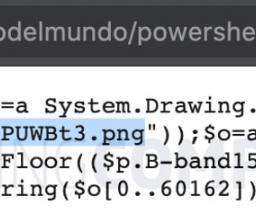
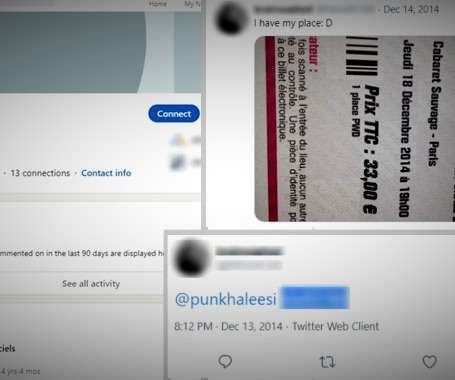
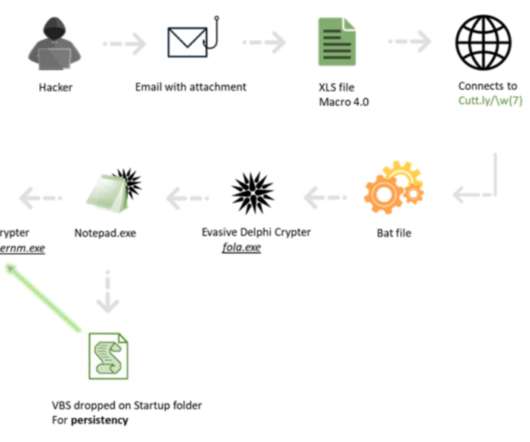
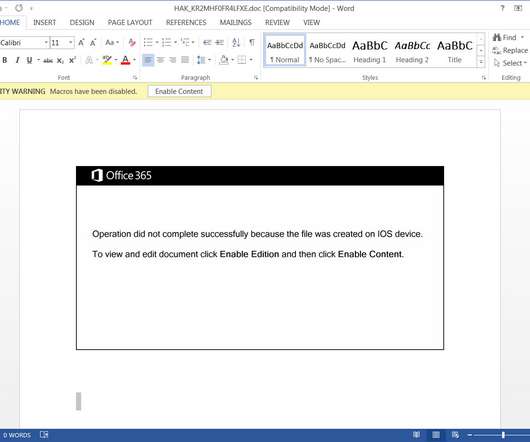
The FBI warns of a significant increase in scams involving free online document converters to infect users with malware. The FBI warns that threat actors use malicious online document converters to steal users sensitive information and infect their systems with malware. ” reads the alert. ” reads the alert.








































Let's personalize your content