Practical coexistence attacks on billions of WiFi chips allow data theft and traffic manipulation
Security Affairs
DECEMBER 13, 2021
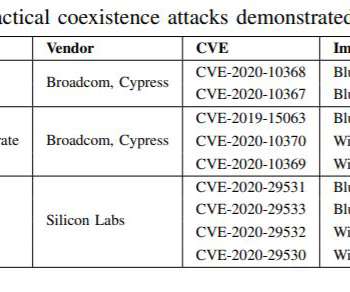
According to the research paper published by the experts, modern mobile devices use separate wireless chips to manage wireless technologies, such as Bluetooth, Wi-Fi, and LTE. The researchers explained that it is possible to use these shared resources to launch lateral privilege escalation attacks across wireless chip boundaries.


























Let's personalize your content