Flaws in mobile Internet protocol GTP allow hackers to target 5G users
Security Affairs
JUNE 15, 2020
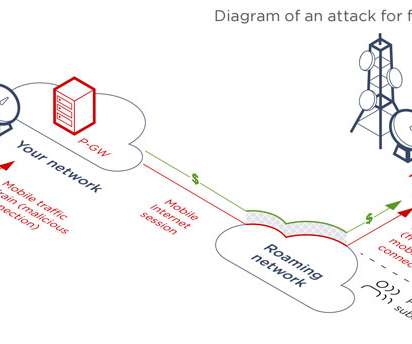
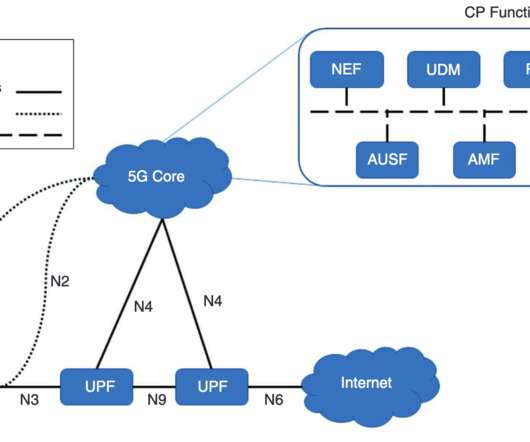
5G networks use EPC as the core network for wireless communications, for this reason, the vulnerabilities discovered by the experts could affect 5G users too. The second architectural flaw is related subscriber credentials that are checked on S-GW (SGSN) equipment by default. ” continues the report. .” Pierluigi Paganini.












































Let's personalize your content