Protecting Against Attacks on NTLM Authentication
Security Boulevard
MARCH 18, 2024
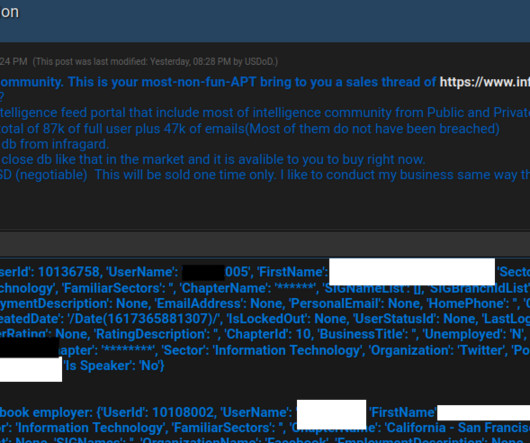
Last week, Microsoft said in an SEC filing that that information stolen in a hack of senior leaders’ email accounts is now being used to “gain or attempt to gain access” to company source code repositories and other internal systems. The post Protecting Against Attacks on NTLM Authentication appeared first on Security Boulevard.







































Let's personalize your content