MyBook Users Urged to Unplug Devices from Internet
Krebs on Security
JUNE 25, 2021
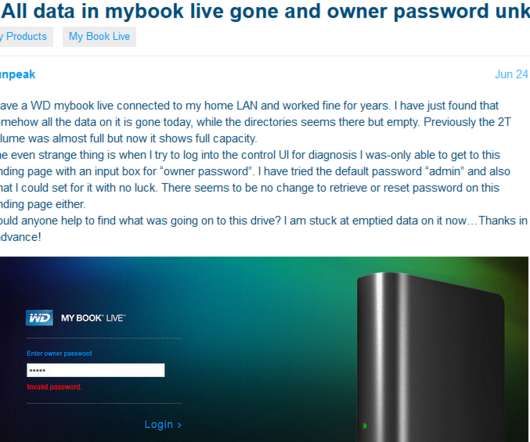
The My Book Live and My Book Live Duo devices received its final firmware update in 2015. That response also suggested this bug has been present in its devices for at least a decade. . “In some cases, this compromise has led to a factory reset that appears to erase all data on the device.




























Let's personalize your content