A Step-by-Step Guide to Cybersecurity Risk Assessment
Heimadal Security
MARCH 15, 2022
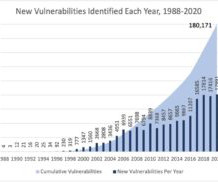
The process of detecting cyber vulnerabilities (software or hardware that might be exploited) and cyber dangers is known as cyber security risk assessment. Why Should You Do a Cybersecurity Risk Assessment? The post A Step-by-Step Guide to Cybersecurity Risk Assessment appeared first on Heimdal Security Blog.



















































Let's personalize your content