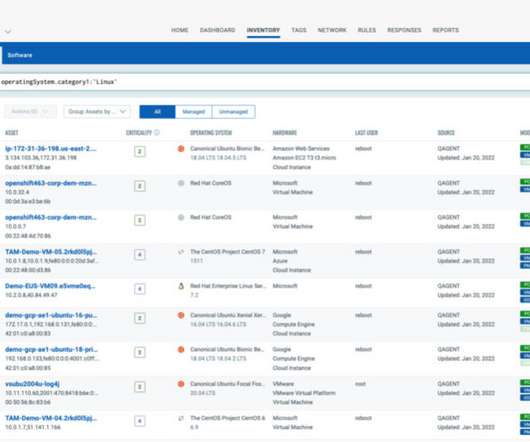
12 Best Vulnerability Management Systems & Tools 2023
Heimadal Security
OCTOBER 26, 2023
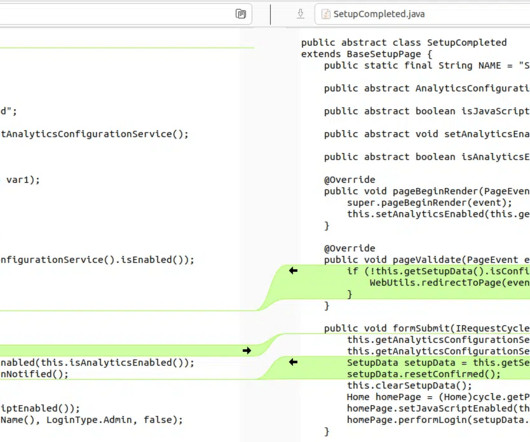
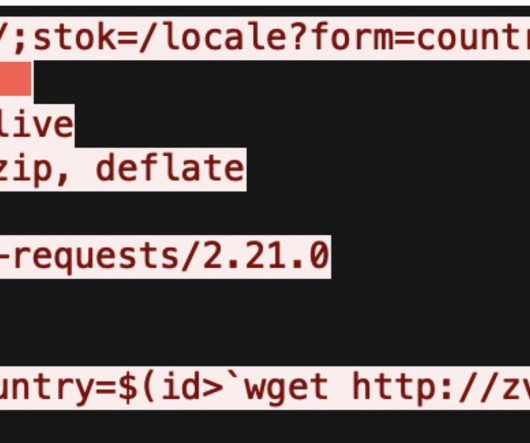
Industry reports highlight the urgency: malicious actors can exploit a vulnerability within just 15 days of its discovery (CISA). The longer you wait, the larger the target on your back grows.












































Let's personalize your content