Colorado Privacy Act – Blog Series (Part III)
TrustArc
JUNE 30, 2021
This is part III in a four-part series on the Colorado Privacy Act.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 category privacy
category privacy  Blog Related Topics
Blog Related Topics 
TrustArc
JUNE 30, 2021
This is part III in a four-part series on the Colorado Privacy Act.

Adam Shostack
OCTOBER 9, 2019
Continuum has a blog and a spreadsheet on threat modeling lambdas (as a category, not specific to Amazon Lambda), and also a post on threat modeling with CAPEC. There’s some context from Aaron Small, who made the project happen. What else have you seen? I’m hoping to find time to write more deeply on several of these.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Adam Levin
DECEMBER 5, 2018
The Mozilla Foundation has released the second installation of *Privacy Not included, the organization’s annual privacy guide to internet-connected gifts. The list was started to promote the idea that privacy and security by design can and should be a major selling point. At the very bottom of the “Not Creepy” list?

Centraleyes
APRIL 22, 2024
NIST Special Publication 800-53, “Security and Privacy Controls for Federal Information Systems and Organizations,” complements FIPS-199 by providing a catalog of FISMA controls for different impact levels. The idea is that the security category should reflect the most significant potential impact.
Centraleyes
FEBRUARY 1, 2024
2023 marked a surge in comprehensive state data privacy laws. At the beginning of the year, only five states—California, Colorado, Virginia, Utah, and Connecticut—had comprehensive data privacy legislation. By the end of the year, the number of states with privacy laws more than doubled.

The Last Watchdog
OCTOBER 17, 2022
To provide even further insight into the data safety and privacy practices of app developers, researchers at Incogni conducted a study of the top 500 paid and top 500 free Google Play Store apps. Among the app categories, shopping, business, and food & drink were found to be sharing the most user data. Greediest data harvesters.

CyberSecurity Insiders
JUNE 30, 2021
This means that the entire roster of (ISC)² certifications are now required for different security workforce categories within the Department, depending on the functional area the role covers. The HCISPP has been approved for the following categories: Information Assurance Manager Level 1 (IAM 1). IAM Level II (IAM II).

Lenny Zeltser
SEPTEMBER 13, 2023
Preparing for cybersecurity and data privacy incidents involves creating checklists and documented plans to enable the response team to do their best during the incident. I’m happy to share the public version of this template with the community in this blog post. What was the root cause? What was and remains to be done?

Thales Cloud Protection & Licensing
DECEMBER 11, 2023
This blog will explain how Thales is enhancing CipherTrust Data Discovery and Classification (DDC) with ML models that help analyze data, learn from insights, and improve results. CipherTrust DDC is pre-built with more than 250 infotypes (entities), covering the vast majority of regional and global data privacy laws and regulations.

BH Consulting
MARCH 8, 2024
This meant, de facto , the Irish privacy regulator was responsible for overseeing the likes of Facebook/Meta, Twitter/X and many others. She also held the role at a time when the EU General Data Protection Regulation came into force, ushering in an increased public awareness of data privacy.
Elie
DECEMBER 12, 2019
This ruling establishes a right to privacy, whereby individuals can request that search engines delist URLs across the Internet that contain “inaccurate, inadequate, irrelevant or excessive” information uncovered by queries containing the name of the requester. This blog post details our. Right to be Forgotten” (RTBF).

Cisco Security
MARCH 11, 2021
Part 1: Top threat categories. Our Threat Trends blog series takes a look at the activity that we see in the threat landscape and reports on those trends. We’ll look at DNS queries to domains that fall into certain categories of malicious activity, and in some cases specific threats, between January and December of 2020.

Schneier on Security
MARCH 12, 2019
Touted as useful management tools, they can augment biased and discriminatory practices in workplace evaluations and segment workforces into risk categories based on patterns of behavior. Remote monitoring and time-tracking used to manage workers and measure performance remotely.

BH Consulting
AUGUST 25, 2021
This blog will look at the issue relating to employee data. The regulation has specific safeguards when processing what is known as special category personal data. As Article 9 makes clear, this category includes biometric data like fingerprints. Include a transparency section in the privacy policy for data subjects.

Centraleyes
APRIL 23, 2024
This section seeks to objectively explore specific categories of digital risks, unraveling strategic approaches to mitigate them effectively. Data Privacy Risks Data privacy risks involve the unauthorized access, use, or disclosure of sensitive personal information.

Identity IQ
JANUARY 17, 2023
What To Know About Privacy Data. Staying safe on the internet means knowing what privacy data is and how to help protect your personal information. In this blog, we will take a closer look at what privacy data is and share details about how you can keep yourself safe. What Is Privacy Data? IdentityIQ.

Security Affairs
MAY 26, 2022
Tails is a security and privacy-oriented Linux distribution, it is a portable operating system that protects against surveillance and censorship. Please vote for Security Affairs and Pierluigi Paganini in every category that includes them (e.g. . “ We recommend that you stop using Tails until the release of 5.1 (May

The Last Watchdog
JANUARY 27, 2022
They can be divided into two categories: Pre-Close Risks. The transition process needs to account for: •Data privacy, ownership, and governance. Lack of clear direction on data privacy and ownership can quickly snowball into a much larger compliance, customer retention, and incident handling issue. Post-Close Risks.

BH Consulting
AUGUST 16, 2023
Curated advice, guidance, learning and trends in cybersecurity and privacy, as chosen by our consultants. Privacy progress: Dr Valerie Lyons’ book publication and award nomination Congratulations to BH Consulting chief operations officer Dr Valerie Lyons, who will become a published author later this year.

CyberSecurity Insiders
JULY 2, 2021
This means that the entire roster of (ISC)² certifications are now required for different security workforce categories within the Department, depending on the functional area the role covers. The HCISPP has been approved for the following categories: Information Assurance Manager Level 1 (IAM 1). IAM Level II (IAM II).

Centraleyes
DECEMBER 4, 2023
This marked a significant milestone, shaping global data privacy and setting the stage for enhanced regulations within Germany. But what does this mean for data subjects, and how can they enforce their privacy rights? This blog post will dive into these questions, providing all the essential details.
Security Affairs
JUNE 13, 2022
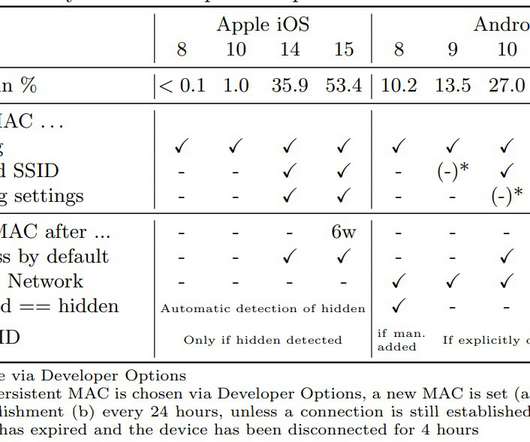
” The following table shows privacy features for probe requests in different mobile OSs: The experts recommend users remove SSIDs that they no longer use, disable auto-join networks, and silence probe requests. Since they can contain sensitive data, they should be sent more carefully and with privacy in mind.”

BH Consulting
JANUARY 11, 2022
In that spirit, we’ve rounded up five of our most popular blogs from the past year. From ransomware and scams to security frameworks and employee privacy, our 2021 ‘greatest hits’ show how broad the areas of cybersecurity and data protection can be. Under the GDPR, fingerprints fall under the category of biometric data.
Security Affairs
JUNE 8, 2022
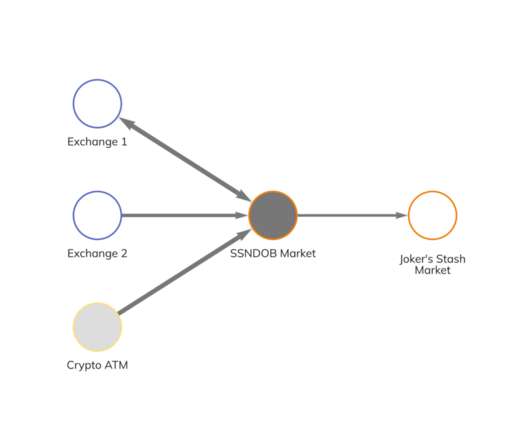
Dismantling illicit marketplaces that threaten the privacy and security of the American public is a priority of the FBI.”. Please vote for Security Affairs and Pierluigi Paganini in every category that includes them (e.g. I ask you to vote for me again (even if you have already done it), because this vote is for the final.
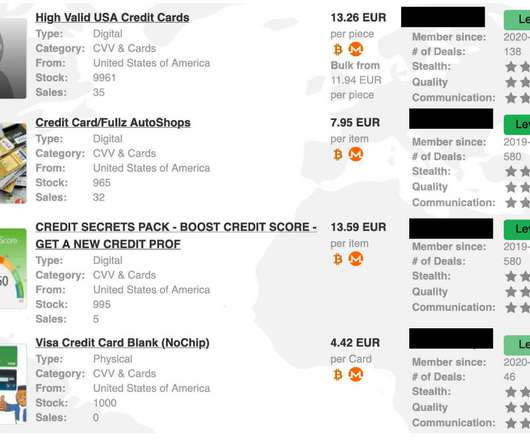
Security Affairs
JUNE 15, 2022
Privacy Affairs published the Dark Web Index, an analysis of prices for illegal services/products available in the black marketplaces and related to the period between February 2021 and June 2022. Please vote for Security Affairs and Pierluigi Paganini in every category that includes them (e.g. To nominate, please visit:?.

Elie
FEBRUARY 26, 2018
This ruling establishes a right to privacy, whereby individuals can request that search engines delist URLs from across the Internet that contain “inaccurate, inadequate, irrelevant or excessive” information surfaced by queries containing the name of the requester. This blog post summarizes our. millions URLs delisting requests.

Cisco Security
MARCH 11, 2021
Our Threat Trends blog series takes a look at the activity that we see in the threat landscape and reports on those trends. We’ll look at DNS queries to domains that fall into certain categories of malicious activity, and in some cases specific threats, between January and December of 2020. Organizations and malicious DNS activity.

The Last Watchdog
DECEMBER 5, 2019
My primer on the going forward privacy and security implications of IoT — What Everyone Should Know About the Promise and Pitfalls of the Internet of Things — won second place in the contest’s IoT Security category. I’ve never done stories to win awards. That said, it is always nice to be recognized by my peers.

Centraleyes
MARCH 6, 2024
Data Stewardship : Respecting privacy rights, ensuring data integrity, and responsibly managing data throughout its lifecycle. Define explicit data categories deemed unacceptable for inclusion in AI models. These pillars encompass key principles such as explainability, fairness, robustness, transparency, and privacy.

Centraleyes
JANUARY 24, 2024
However, transparency does not inherently guarantee accuracy, privacy, security, or fairness, underscoring the need for a balanced approach. Privacy-Enhanced Privacy is a fundamental consideration in AI design, development, and deployment.

Thales Cloud Protection & Licensing
AUGUST 15, 2019
375 the California Consumer Privacy Act (CCPA), making California the first U.S. state to pass its own data privacy law. Last August, my colleague Ashvin Kamaraju wrote a blog shortly after this took place. 5) The right of Californians to equal service and price, even if they exercise their privacy rights.

Troy Hunt
DECEMBER 24, 2019
— Jason Antman (@j_antman) December 9, 2019 As I said in the intro to the PDL blog post, the pattern of data being collected via data aggregators then being redistributed outside their control (whether you call it a "leak", a "spill" or a "breach") is becoming alarmingly common.

Security Boulevard
NOVEMBER 2, 2021
HIPAA Security Rule is broken down into three categories of safeguards: Administrative : policies and procedures for putting security and privacy measures in place to protect electronic PHI (ePHI). Further HITECH applied the HIPAA Security and Privacy Rules to business associates, culminating in the consolidated Omnibus Rule in 2013.

Centraleyes
NOVEMBER 16, 2023
SOC 2, short for System and Organization Controls 2, is an independent audit and certification that evaluates an organization’s information systems security, availability, processing integrity, confidentiality, and privacy controls. Privacy: Managing personal information in line with privacy principles defined by relevant authorities.

SiteLock
AUGUST 27, 2021
Almost Half of Leading Websites Fail Security and Privacy Tests. The OTA evaluated these websites based on criteria in mainly three categories: consumer protection, privacy and security. Follow the SiteLock blog for the latest cybersecurity news.

NopSec
MAY 4, 2022
Security teams need to get ahead of potential threats such as ransomware attacks , privacy invasions, exploitations of common vulnerabilities, and the like. To manage what feels like chaos requires breaking down the dangers in categories and managing accordingly. We’ll look at that in detail in our next blog.

Centraleyes
MARCH 18, 2024
Quick Start Guides New users can now learn from others’ successes and select their area of interest from a newly compiled set of case studies and easily navigable manuals designed for particular user categories, such as small businesses, corporate risk managers, and organizations looking to strengthen their supply chains.

BH Consulting
DECEMBER 14, 2020
This is the second blog in our series on the evolving international transfers landscape following the Court of Justice of the European Union [ CJEU ] decision in July 2020 which ruled the Privacy Shield data transfer mechanism invalid. Adoption of strict and state-of-the art data security and data privacy policies.

The Last Watchdog
JULY 27, 2020
Likewise, the COVID-19 contact tracing app developed by Apple and Google continues to evoke concerns that it will end up leveraging AI to normalize privacy invasion. AI tools are designed to put people into categories, Shashanka says. This column originally appeared on Avast Blog.).

eSecurity Planet
JANUARY 11, 2024
This category also includes routers, switches, and Internet of Things (IoT) devices that can’t install traditional endpoint protection such as antivirus (AV) or endpoint detection and response (EDR) solutions. Email Address By signing up to receive our newsletter, you agree to our Terms of Use and Privacy Policy.

ForAllSecure
FEBRUARY 23, 2023
In this blog post, we'll explore why API security is so important, and how you can make sure you're doing it right. They also provide customer privacy protection and robust security – both of which are vital elements of customer experience and trust. It may mean inventorying API endpoints within your private network.

BH Consulting
JULY 14, 2021
Curated advice, guidance, learning and trends in cybersecurity and privacy, as chosen by our consultants. Our data protection consultant Tom Knierim pondered this very problem, and blogged about it in May. MORE ICS-focused but still plenty of good incident response insights from this SANS blog. Links we liked.

Centraleyes
APRIL 18, 2024
Electronic Evidence Digital data stored on systems, servers, and networks, including log files, configuration settings, and other digital artifacts, encompass this category. Use well-defined categories and labels to make it simple for auditors to locate appropriate and sufficient audit evidence.

Thales Cloud Protection & Licensing
FEBRUARY 19, 2019
It’s no longer just data center applications – cloud implementations, big data, IoT, mobile payments, containers and blockchain are on the list for implementation by year end for 80%+ deployment in each category. The post 2019 Thales DTR: Global Edition: Facts that may surprise you appeared first on Data Security Blog | Thales eSecurity.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content