T-Mobile Investigating Claims of Massive Data Breach
Krebs on Security
AUGUST 16, 2021
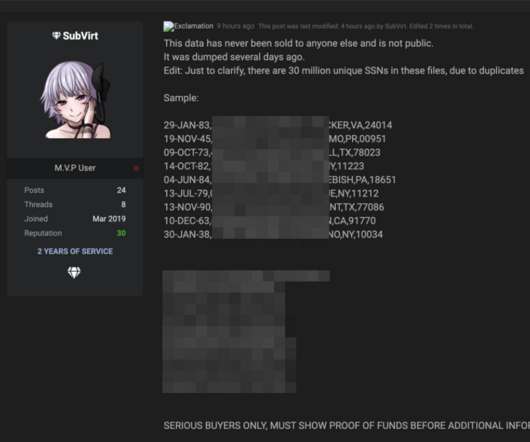
On Sunday, Vice.com broke the news that someone was selling data on 100 million people, and that the data came from T-Mobile. On Sunday, Vice.com broke the news that someone was selling data on 100 million people, and that the data came from T-Mobile. A sales thread tied to the allegedly stolen T-Mobile customer data.













































Let's personalize your content